The Shape Of Cyberspace
Republishing this AGAIN.
Our species evolved as hunter gatherer bands on African savannas. Science marks the beginning of our line with homo erectus, but I speculated in Gamma Draconis Rising that maybe the cascade that led to us began with homo habilis, and the El Tanin asteroid, which may have had something to do with our current ice age.
I could go on all day about Denisovans, Neanderthals, homo floresiensis, and the extraordinary find of homo naledi in the aptly named Star Chamber. But we’re going to get your tuber digging, big cat dodging hominid brains acquainted with the natural boundaries of cyberspace.
Attention Conservation Notice: I write this article every couple years, most recently as The Shape Of Cyberspace. If you’re already comfortable employing Tor, VPNs, and the like, you can just skip this.
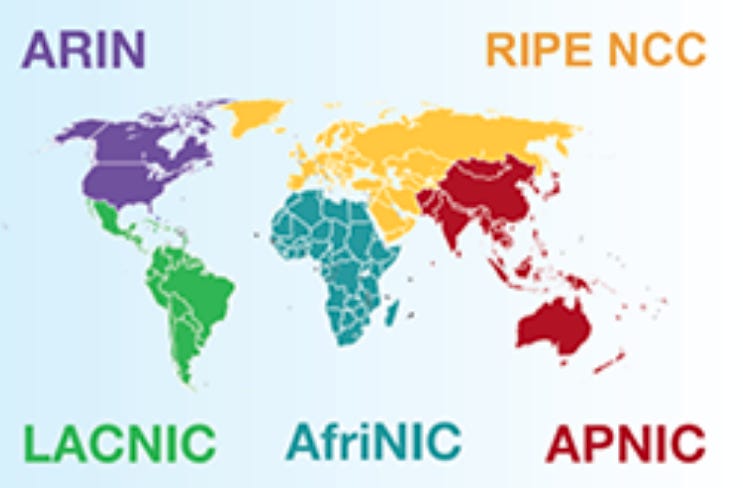
Global Topology:
Let’s start with that internet usage cartogram as a foundation. Instead of sizing land by geographic area, this sizes it by internet usage.
The internet at its very top level is composed of five Regional Internet Registries. Think of them as digital tectonic plates. Oceans are no barrier thanks to undersea cables and each connects with all the others at dozens of peering points. Once there were peering points akin to the role the Mideast plays, the crossroads of three continents. Over the years as traffic grew so did the mesh connecting the regions. I do not believe there is a single point of failure any more, that stopped being a thing maybe twenty years ago.
These five entities are responsible for one or more blocks of sixteen million IP addresses from the original 32 bit IPv4 address space. Now that 128 bit IPv6 addresses are available things are changing quickly, but for now the bulk of where things are hosted for westerners still resides in the original IPv4 space. The RIRs are also responsible for the administration of Autonomous System numbers, the unique serial numbers ISPs use.
North American residents can think of the AS number as being akin to our three digit area codes, an IP prefix is like a three digit exchange, and the IP address is akin to a full ten digit phone number.
The RIRs dole out blocks of IP prefixes, which are variable sized blocks of addresses, and AS numbers to ISPs, who then make them available to the world by “announcing” them via the Border Gateway Protocol. The RIRs are administrative entities, the ISPs that operate the Autonomous Systems are what actually make the bits fly.
If you want to get a visual of this, Hurricane Electric’s BGP Looking Glass is the slickest tool out there and North Korea’s AS131279 is small enough for a complete newcomer to get their head around it without too much trouble.
Here’s a phone number to IP address comparison. If you want to call the Central Intelligence Agency, you would use:
Area Code: 707
Exchange: 967
Number 2500
If you want to send them an email, your mail server has to turn cia.gov into an IP address, in this case 198.81.129.68.
AS: 7046 MCI dba Verizon Business
Prefix: 198.81.128.0/18
IP 198.81.129.68
That /18 is Classless InterDomain Routing notation. The smallest CIDR block a RIR will give an ISP is a /24 - a group of 256 addresses. A /23 is 512, a /22 is 1024, and so forth. The /18 is a block of 16,384 addresses.
Domain Name Service:
When your computer wants to contact something on the internet, it typically sends DNS a name, like nealr.substack.com, and waits for an IP address to be returned, in this case 172.64.154.11. Sticking with the area codes and phone numbers analogy, this is like a phone book.
When you want to create a domain you purchase the rights to one from a Registrar. These entities play the same role with names that the RIRs play with IP addresses. Once there was just one, then a few, and now there are a great many from which to choose. The Registrars periodically publish domains and their authoritative nameservers to the world’s thirteen root nameservers. All the roots know about domain is the identity of the domains’s authoritative nameservers. If you wanted to contact the CIA, your resolver (also a DNS server) would ask the roots about the name cia.gov, and then ask the CIA’s nameservers about details, such as how to reach the web site, or the name of their mail exchanger.
As an end user your perspective on DNS is that you use a name and it gets converted to an IP address. Things start with your resolver, which would be your ISP’s DNS server, or if you’re fancy you might run PI-hole locally to filter things. This talks to root namesevers to get the authoritative nameserver for the destination domain. Your resolver then makes more detailed queries to the authoritative server.
This image from Amazon’s What Is DNS? page is an excellent representation of the flow of activity.
And here’s a handy reference in case you have to troubleshoot stuff.
Content Distribution:
What you’ve seen thus far is how things were from their early days, with DNS arriving in 1984 and the current version of BGP becoming active in 1993. The internet grew massively starting in the mid-1990s, and now there are some additional layer.
Popular web sites generate enormous volumes of traffic and they sometimes need to fend off attacks. Content Distribution Networks, hereafter CDNs, facilitate this. A CDN offers a subscriber an authoritative nameserver to use, a network of caching systems to mirror their web site, and then they layer on a variety of additional tools.
Cloudflare hosts about 10% of the internet in this fashion, Akamai and Fastly are similar services for large players, and when U.S. extremists get in trouble and Cloudflare gives them the boot, they go running to Russia’s DDos Guard. There are a bunch of small, shady CDN operators, and it can be a dirty business - the pack attacks vulnerable sites, and then those sites come to one of the shady CDN operators for help. This can be thought of as … like the mafia, “taxing” vices, or like komodo dragons - the one that bites the deer is not always the one that gets to eat the deer.
Means Of Concealment:
There are a variety of ways to conceal your origin when using the internet. We’ll cover three common methods.
Virtual Private Networks, hereafter VPNs, are a service that provide an encrypted tunnel from your IP to one of theirs, and anything you access can only see the VPN, not your IP address. Some of them offer multiple hops inside their network, to better conceal who is using the system. They all make strident claims about not logging the activity of their clients. Every year another dumb kid makes the news by learning the hard way that this is usually a lie.
The most resistant of the VPN providers, Proton, has only given up a customer once to my knowledge, and it was a curious jurisdiction thing. Someone in Switzerland used Proton’s Swiss assets to commit a crime against another Swiss citizen. Sweden’s Mullvad has never been caught out and they permit anonymous funding of accounts. The extremely feral Cryptostorm also has a lot of features like these, but it’s the Starwars Cantina of providers, best left to natives that understand the culture.
The Onion Router, hereafter Tor, is what most people are talking about when they use the word darknet. The Tor software provides a SOCKS5 proxy on your network and then multiple encrypted hops so that the exit your traffic uses has no idea where the traffic originated. Your software connects to the SOCKS5 proxy, and Tor provides a curious, erratic multihop VPN. Tor gets attacked a LOT. They don’t own the systems that provide services, like the VPN providers do, it’s all purportedly community driven.
There are also legions of “open proxies” out there. These are typically SOCKS5 protocol systems that are either accidentally or intentionally left available. You find a list of them, set your browser to use one of them, and then you are nominally hidden. There is a tool called proxychains, which as the name implies, lets you daisy chain proxies to better conceal yourself. There’s a famous meme about this:
Esoterica:
There are other overlay networks that compete with Tor. I’ve used I2P in the past, but it’s a very closed world, akin to the island of St. Helena - there aren’t a lot of tourists, and one does not casually drop in for a visit. There is a globally distributed anonymized censorship resistant network called IPFS - short of InterPlanetary File System. Freenet is similar to IPFS, but famously infested with child pornography and highly resistant to takedown efforts.
These things have their uses, but for the moment the most you need to know is that they exist.
Conclusion:
We are built at a very deep level to roam open spaces with some trees for shade/shelter and a visible source of water. Bands grouped into clans, clans grouped into tribes, some tribes mastered agriculture, and then created villages. This pattern continued until almost all land on this planet was associated with a given nation state. Our entire conception of the rule of law is rooted in the notion of jurisdiction, a physical nexus for people, things, and events.
The internet completely and utterly breaks all of those ingrained and learned norms, it’s a madhouse of billions of devices connected to a global any to any network only a few hundred milliseconds across. Being the clever apes that we are, we experience this as a “virtual” environment, employing familiar “meatspace” metaphors to describe things. Those deeper things are always there, covered by layers of abstraction.
Trying to sum this up brings another analogy to mind. We place our expectations over the top of the internet, a sort of human version of Newtonian physics we’ve known for centuries. But if you set aside that comfortable framework and look again, it’s akin to encountering quantum physics with its particle/wave duality, entanglement, and action at a distance.
I hope this has provided a digestible lesson on what the internet actually is. Quaint notions like sovereignty and jurisdiction are deeply problematic in the online world, and nation states are troubled by the virtual tribes crossing their porous by design borders. The list of Westphalian states that control their internet while leaving it functional is unitary: China. Russia is trying unsuccessfully to join them, and as a rule when anywhere else has trouble, they resort to simply turning off cellular networks and ISPs until things settle.