Stochastic Espionage Encounter
AI is enabling infiltration at scale on LinkedIn.
Starting December 18th I was subject to a pretext approach that began on LinkedIn. I’ve been letting it sit, as one does, waiting to see what might happen next. Then someone in a geopolitical Signal chat post this piece about Chinese spies approaching the U.K. Free Speech Union, and in that I found the outline of the article I planned to write here, describing the manner of the approach.
This happened after Careless Whisper: Moving Off Signal? was written. Despite the short time frame, I became willing to file this one under espionage, as opposed to hi-tech scammer, on the strength of that other article.
Let’s just dump this one over so you guys can see what I see, and perhaps learn from it.
Attention Conservation Notice:
I am a little fish, a sort of espionage artistè, dancing along the edges of the vortex. Stochastic spying is maybe the new normal in 2025, this is not about lil’ ol’ me, it’s about a system so overcapacity, thanks to AI, it has time to try everyone. That being understood, come on in …
Background:
When I see any sort of pretext approach I am instantly on alert. I have … done things … over the years, most publicly MIOS: Iran’s PressTV. There are some sore asses out there with my size ten boot print on them. So I must watch all the things, just in case there’s payback in the works. This one was obviously problematic right from the start, but I let it run on so I could see the methods, and perhaps to deduce motivation.
Specifically I was interested due to the level of effort:
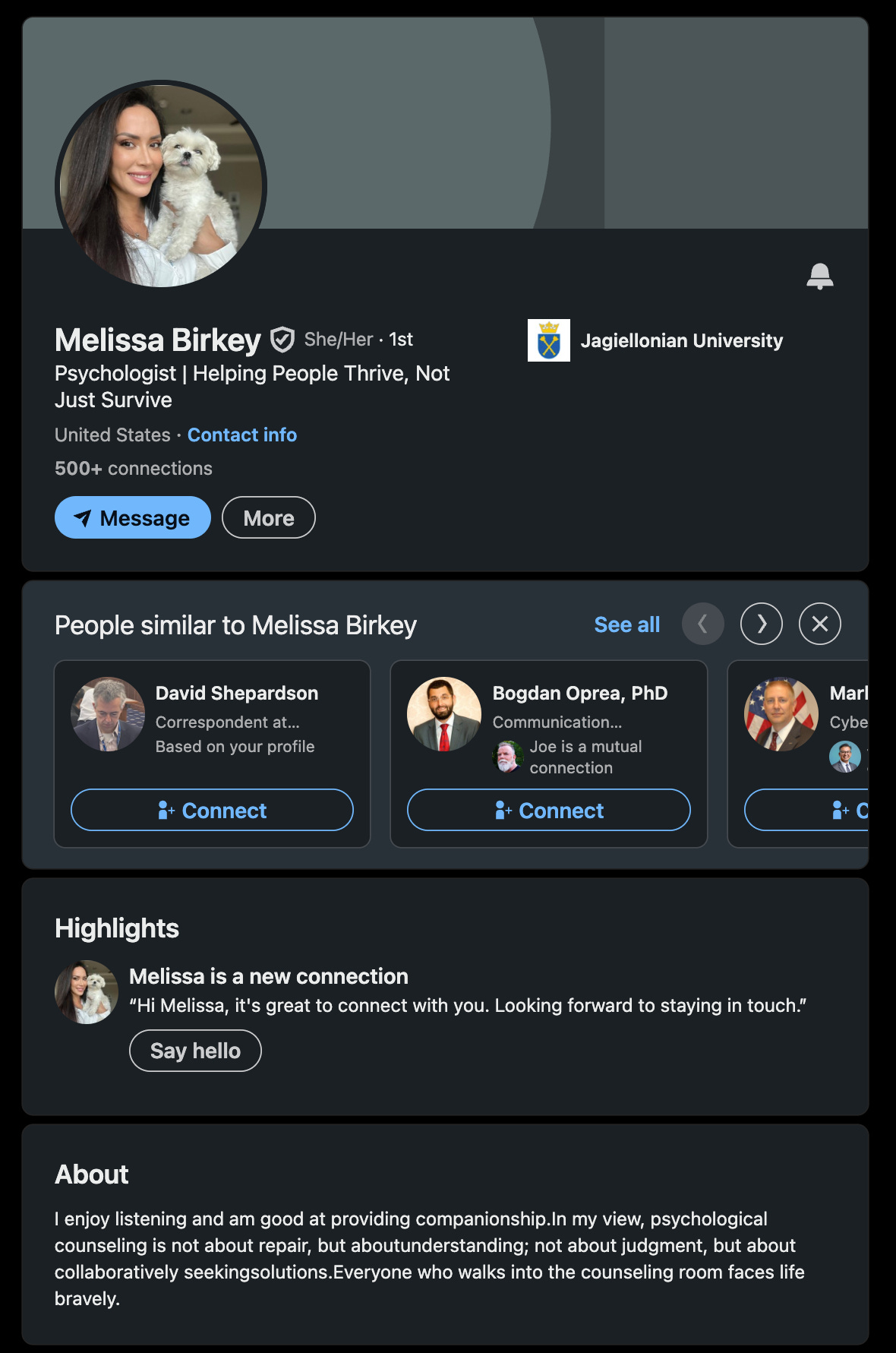
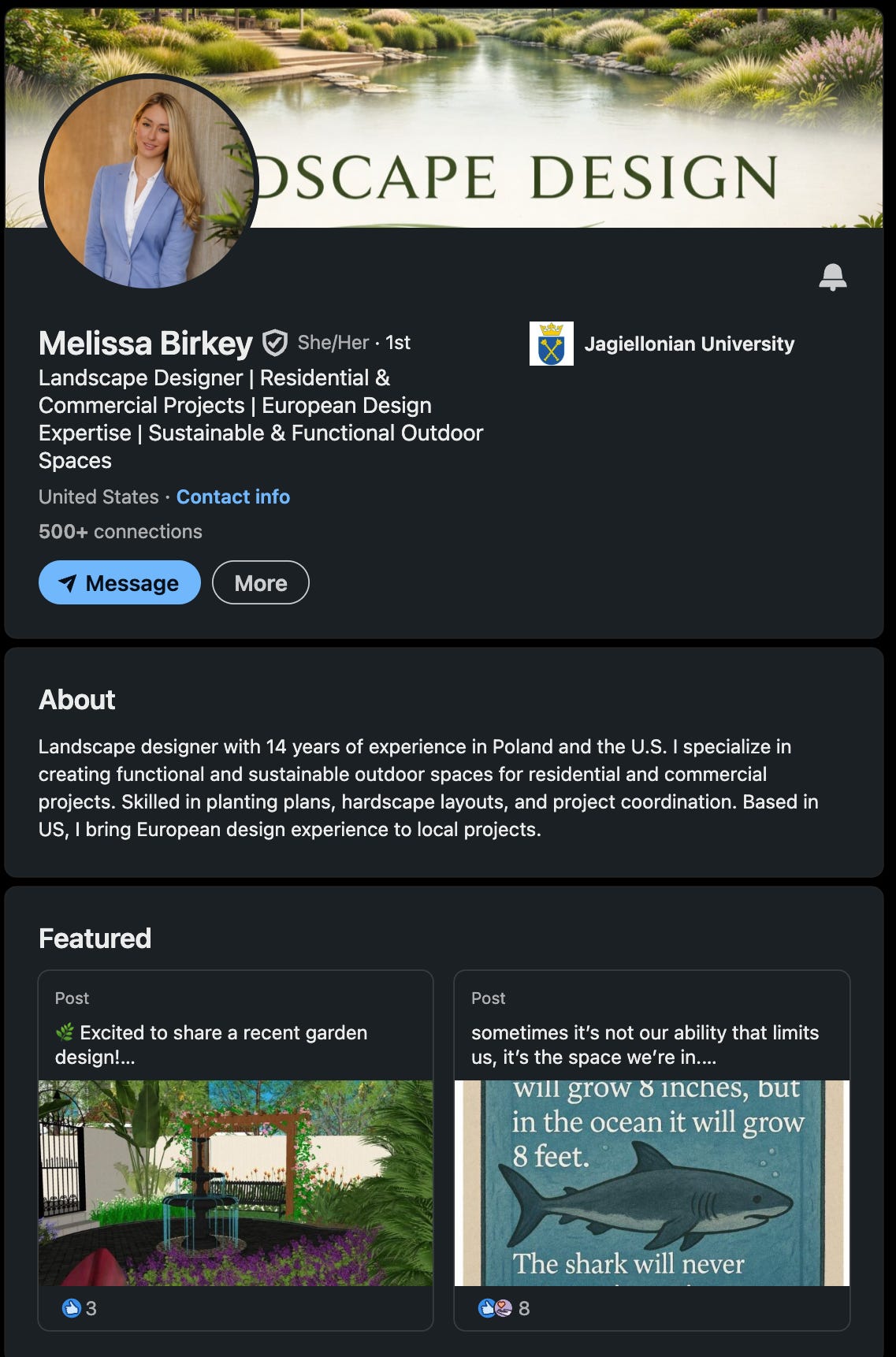
LinkedIn profile with 500+ contacts.
Three year old account.
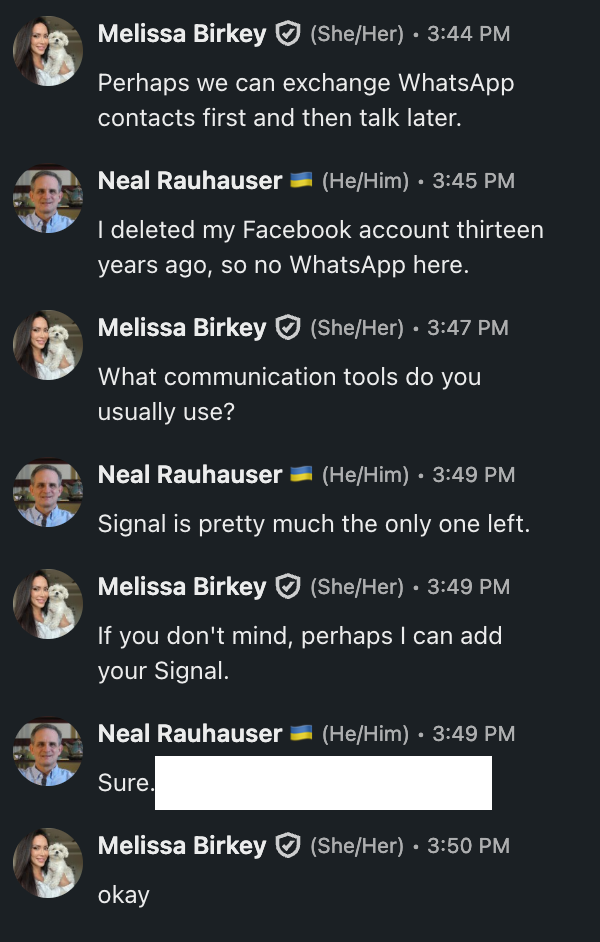
Immediate offer of WhatsApp connection.
Responded, but very slowly, to my Signal suggestion.
Implausible conversation but serious investment obvious.
Wanted to talk domestic U.S. politics.
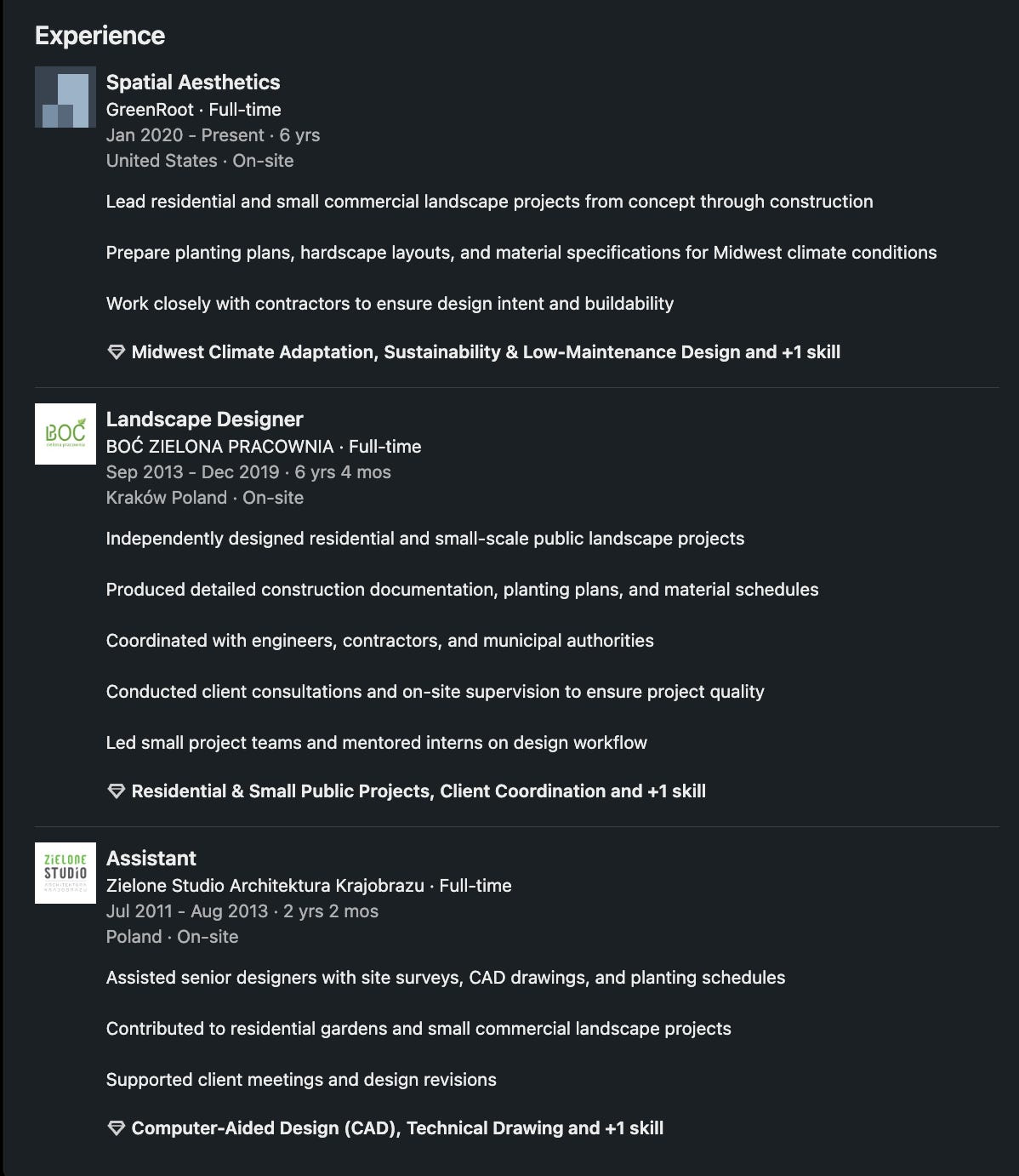
I keep a 500+ contact LinkedIn alter-ego and have for almost a decade now. I don’t think one could plant such a thing today as a lone gun operator. I tried to make another one three years ago and got promptly bounced, despite spending time and money trying to get it right. I have some sense of what it would take to do an account like this and it’s not an asset I would personally throw around casually.
The one I keep is for commercial engagements - divorce/custody, due diligence, harassment/stalking investigations, the sort of work one does for pin money. Losing it would not wreck anything I’m doing in 2026, but I would be quite miffed if that were to suddenly vanish.
So someone created this account, lightly seasoned it, then let it sit for three years. That rules out various ankle biters, and we’ve come to the point where I again get to suggest you read What Hunts You?
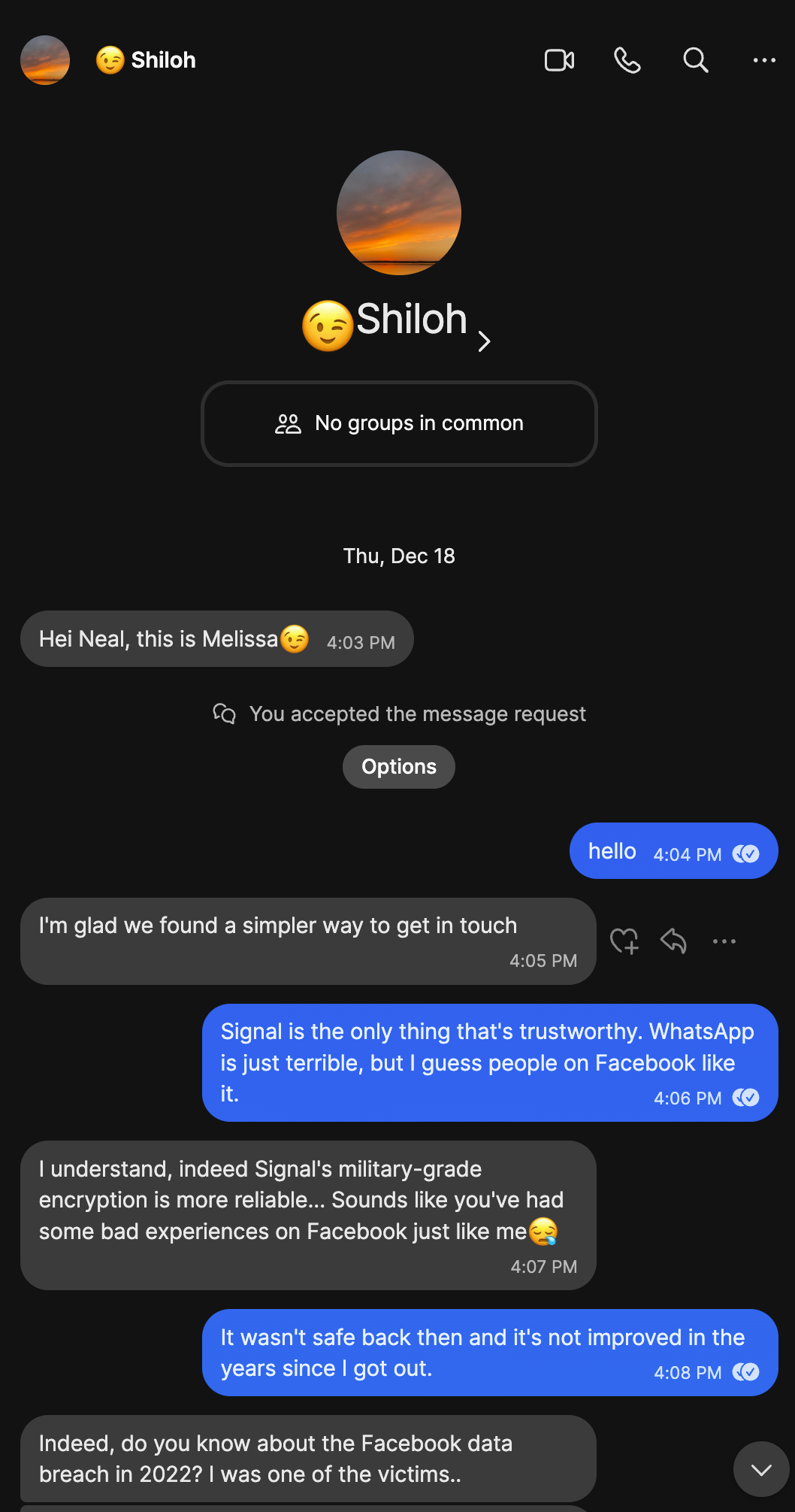
Initial Approach:
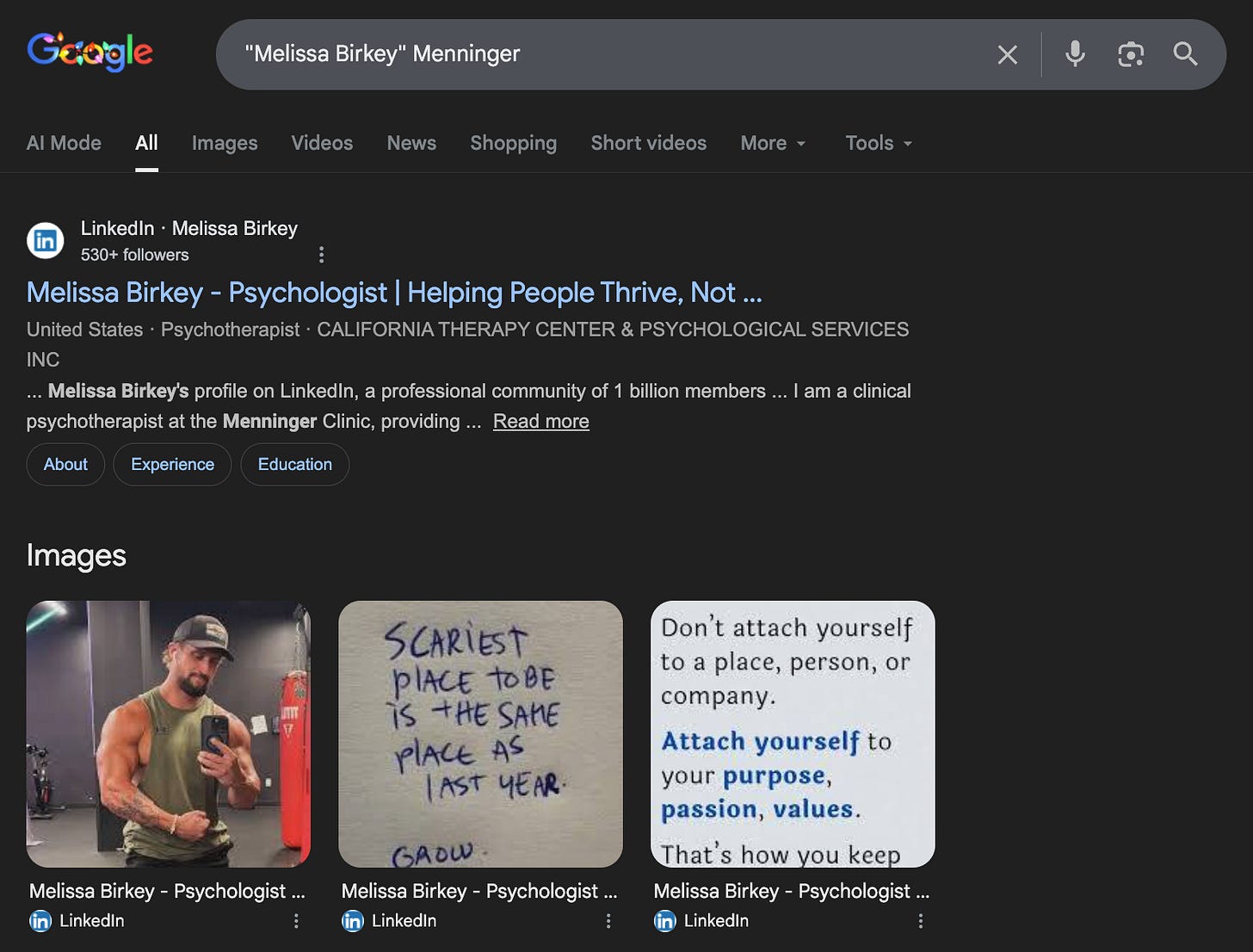
Only one Google hit for the name when combined with her alleged employer.
The company
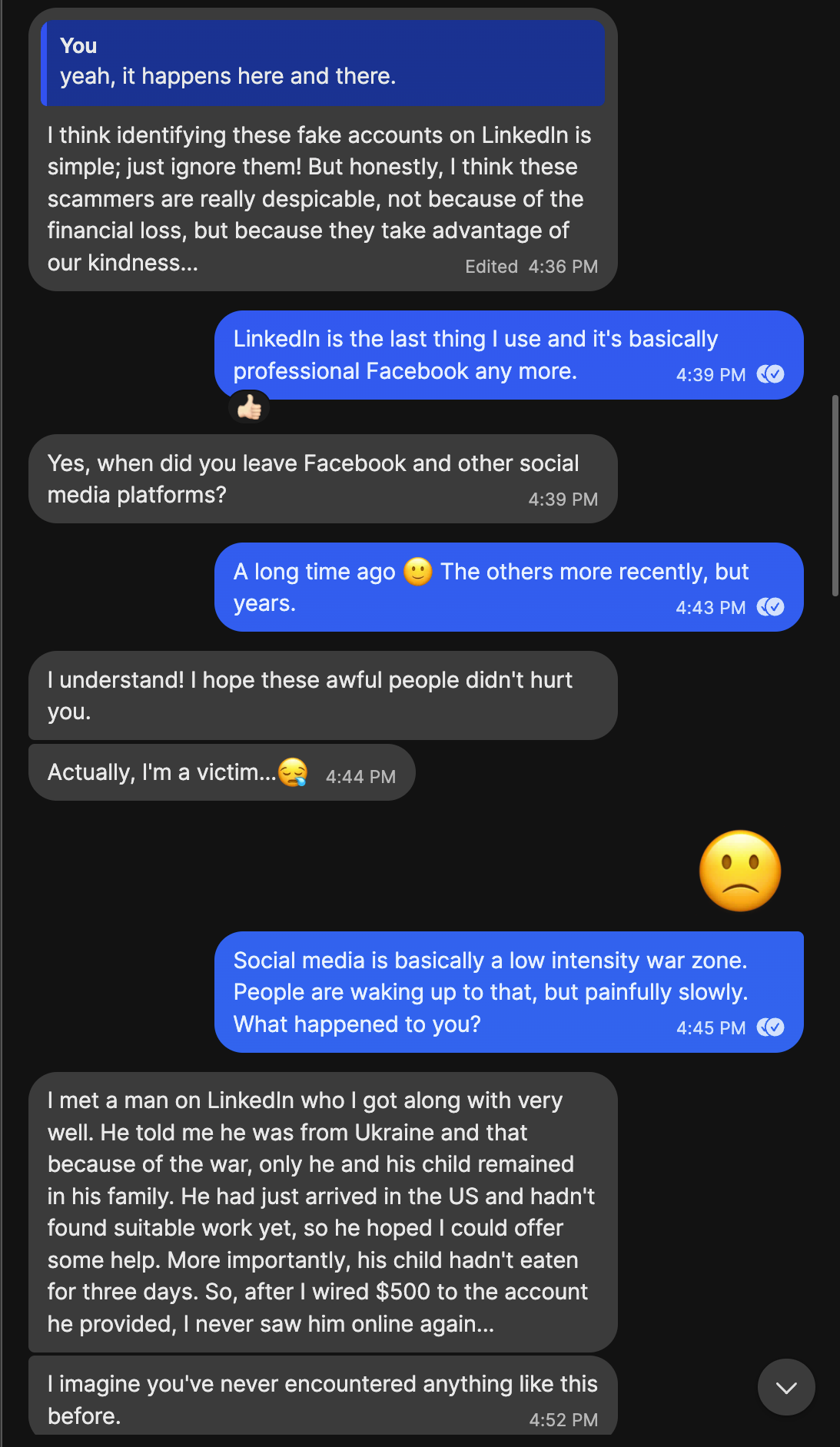
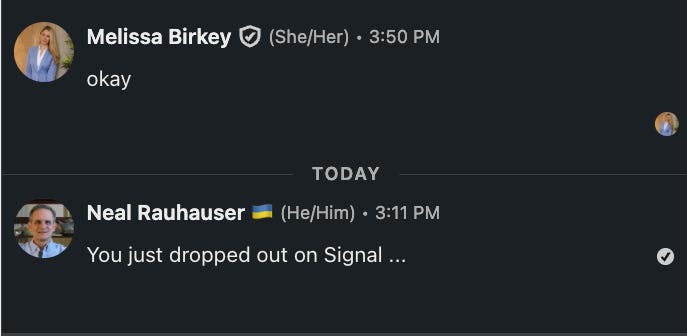
The attempt to move to WhatsApp was basically immediate.
Despite being a ping pong exchange, it took fourteen minutes before “Shiloh” picked up the conversation. I read that as someone working in a call center environment, who expects only WhatsApp, so they handed me off to someone who does Signal.
Takedown:
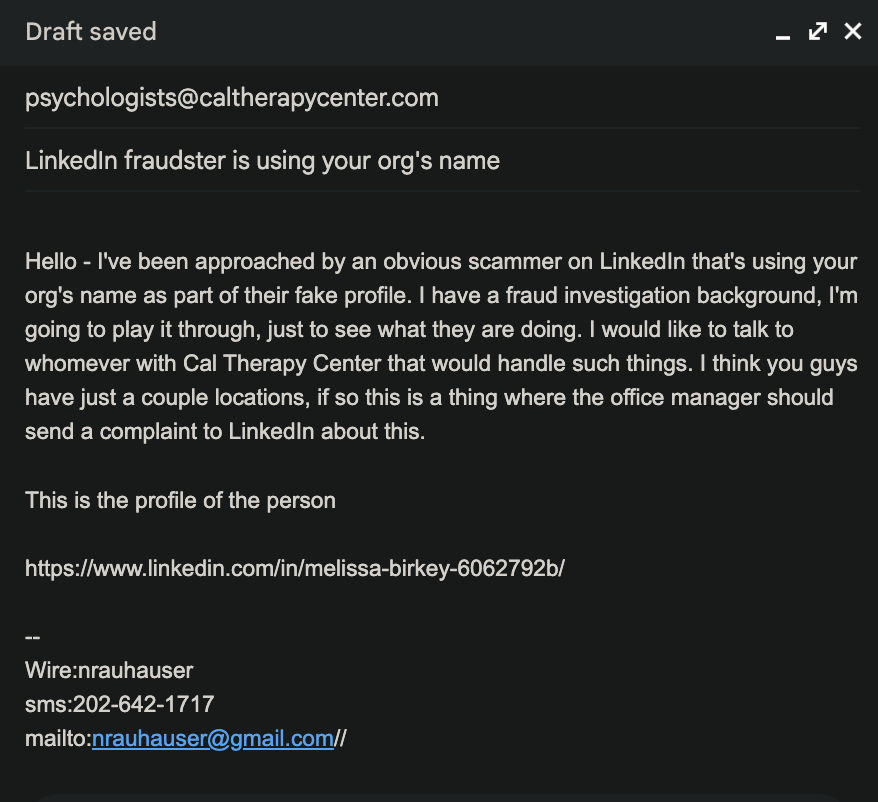
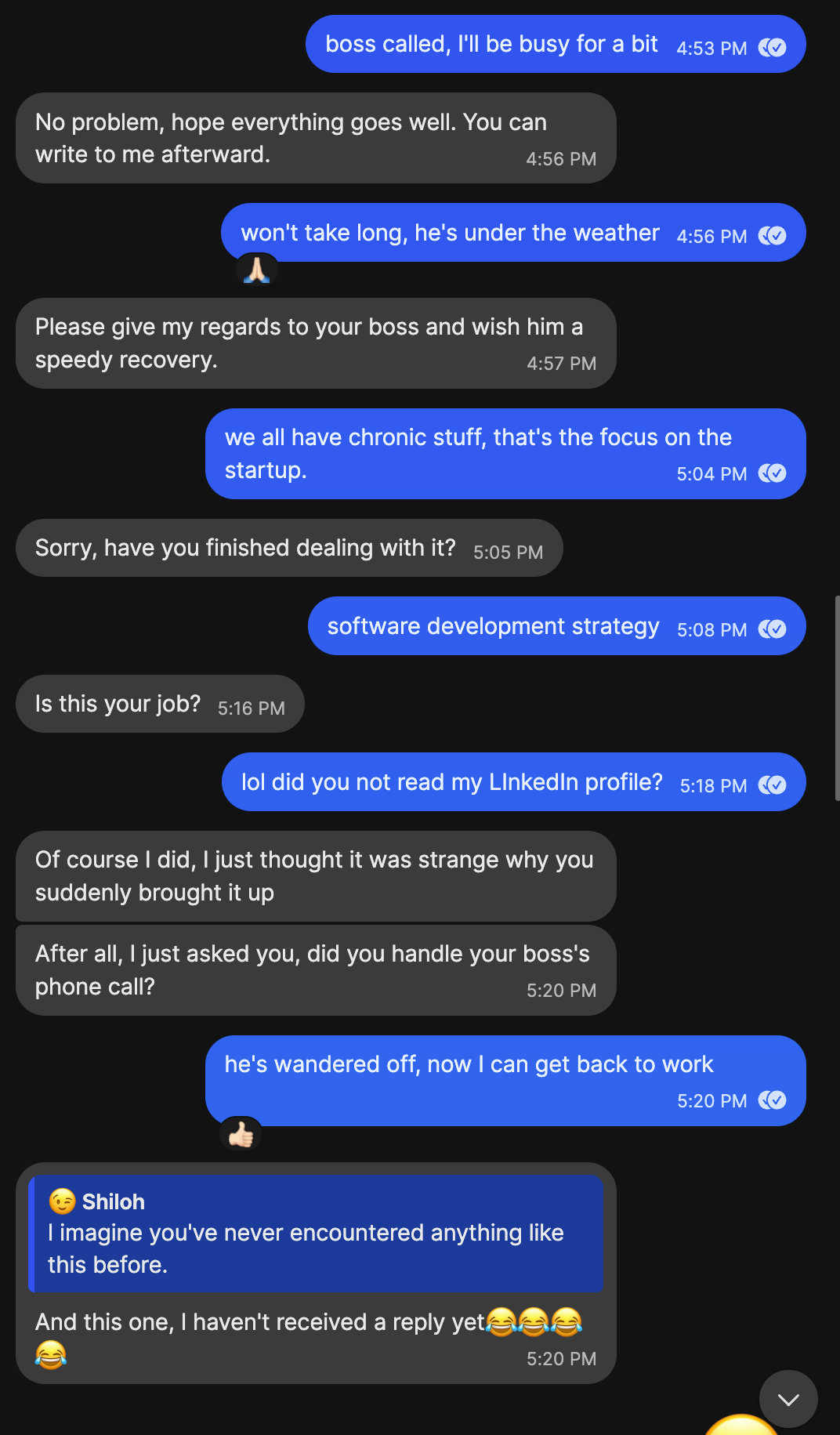
Having made the Signal connection, I decided I would hit the LinkedIn base, just to see what the response would be. By this point it was at bare minimum a serious fraudster, and should not be tolerated, lest someone less wary blunder into it.
This did get a response from the company, and I expected it would just disappear. It did not, as we’ll see after the conversation.
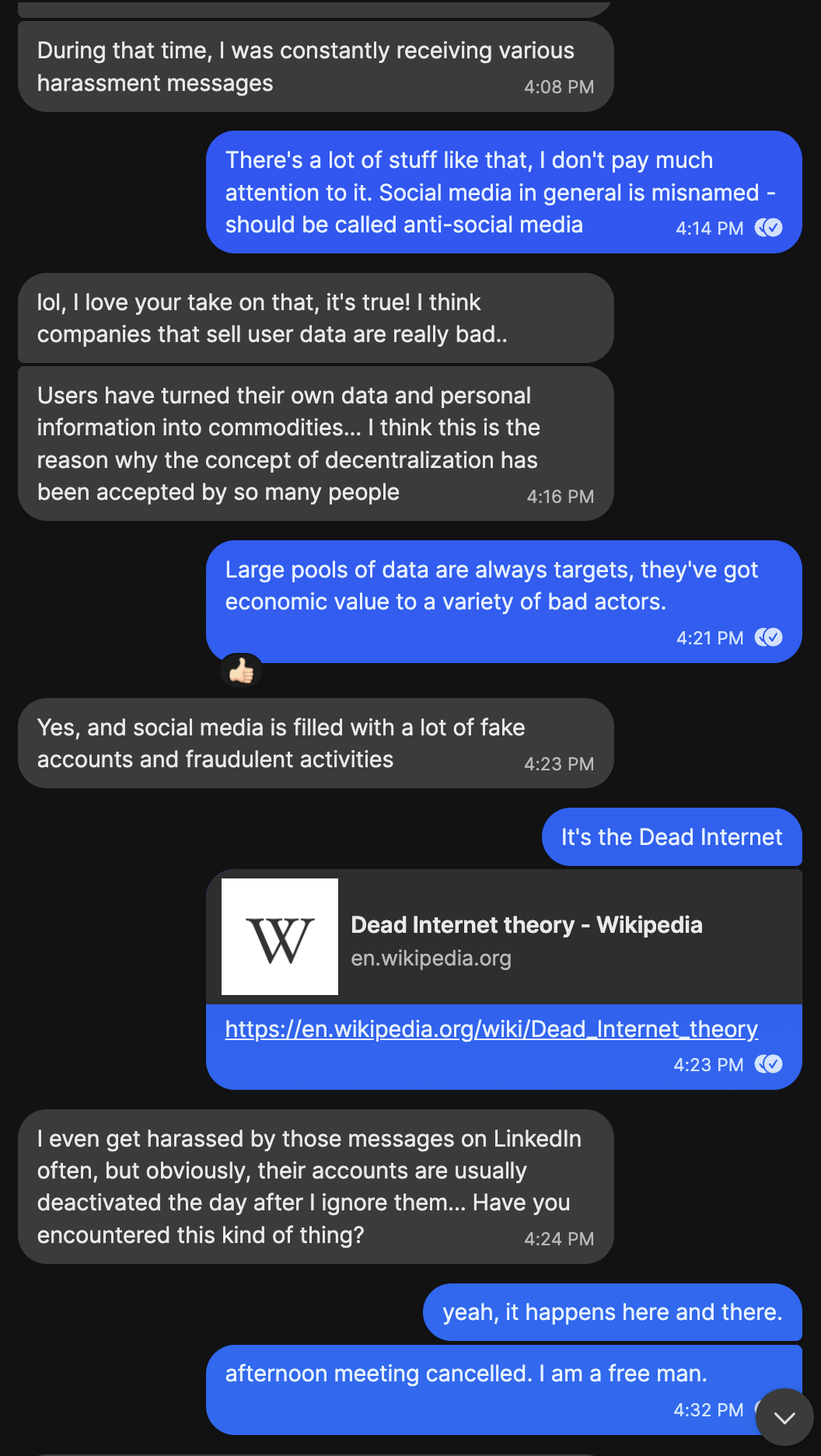
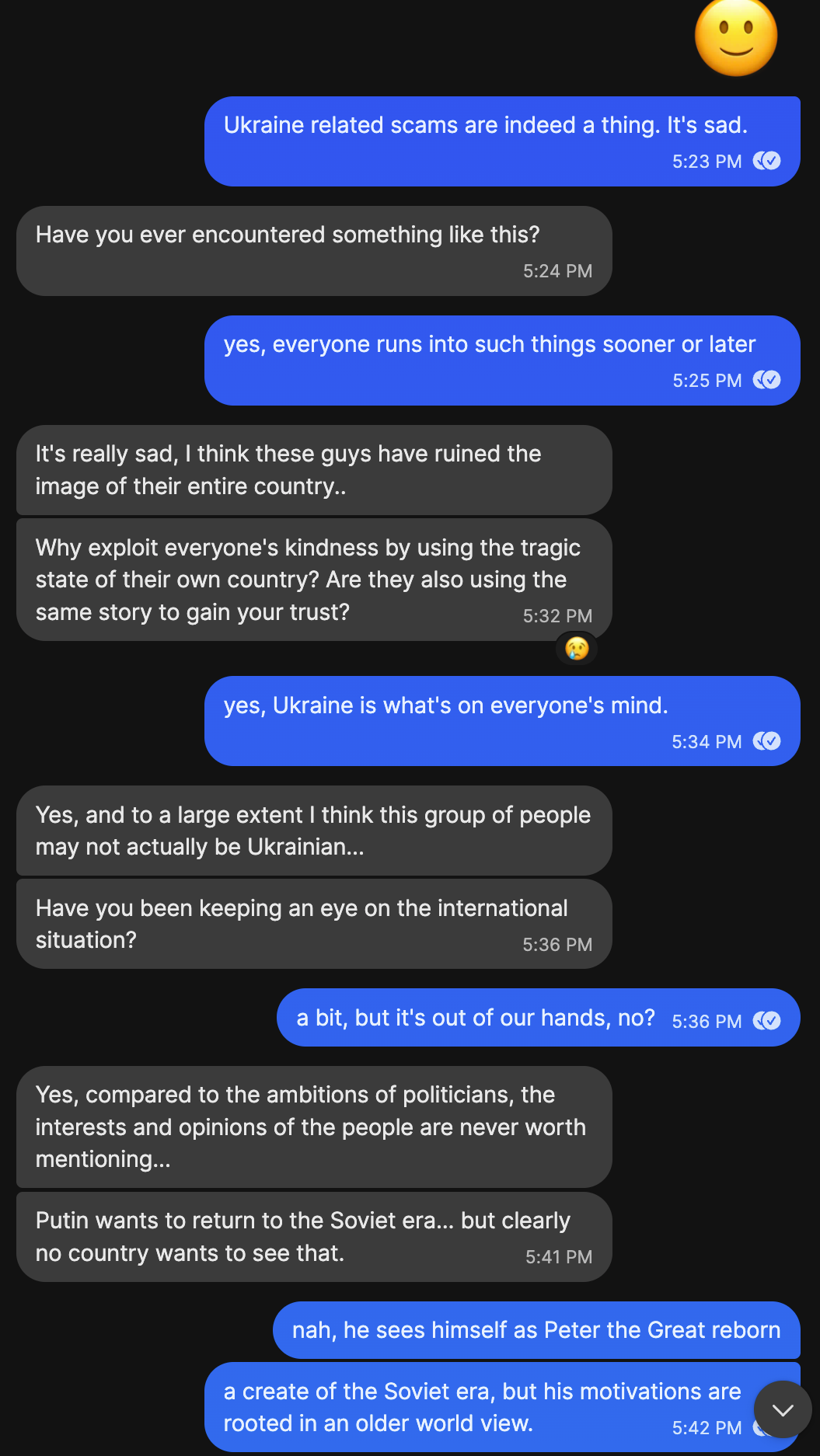
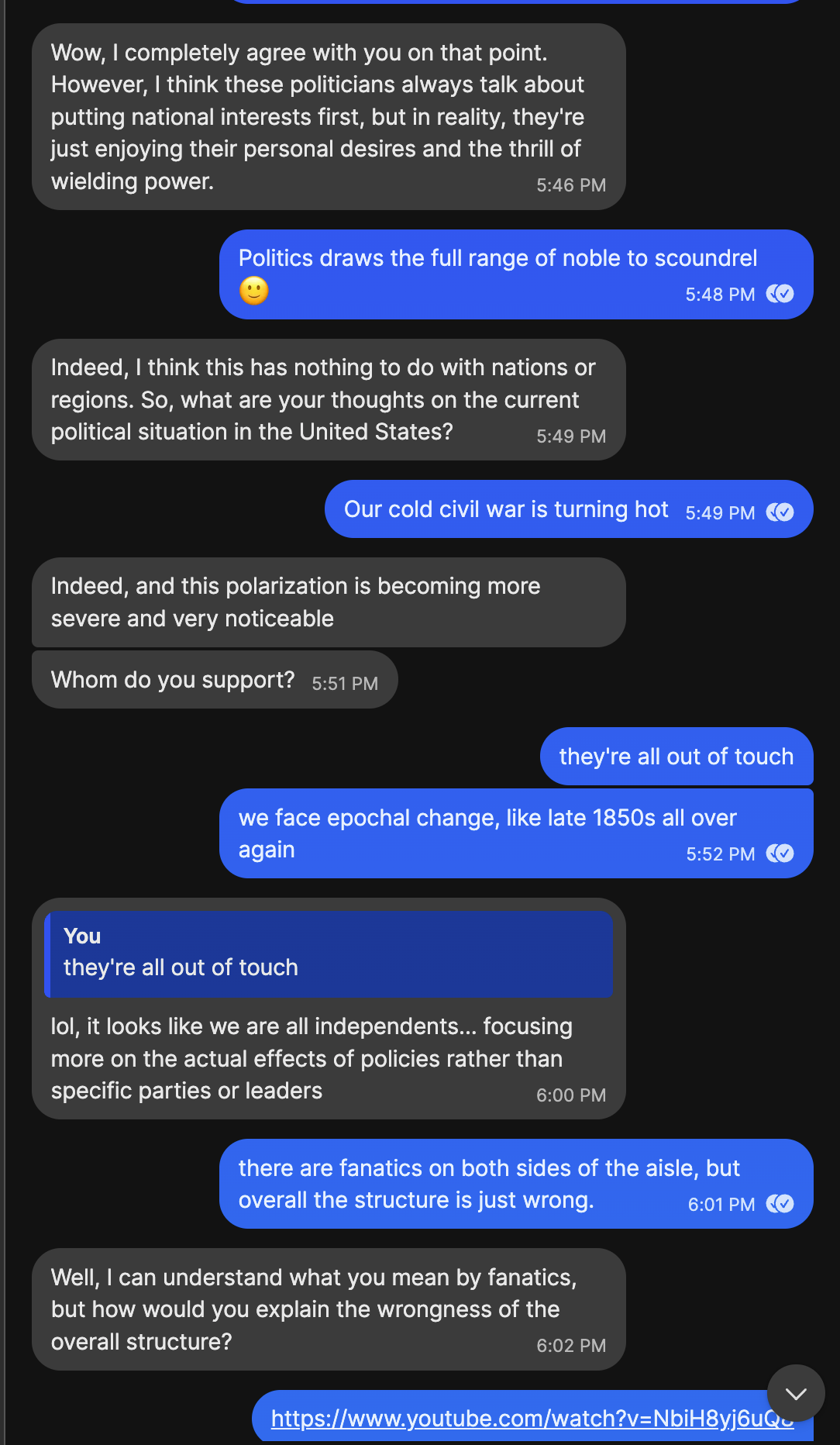
Talking Politics:
Economics video here, about growth = cancer.
And that was the end of that.
Evolution:
Having decided to write this the afternoon of Friday, December 26th, I went back to review, and I found some significant changes.
Brunette + pet gone, blonde but demur and professional. The legend (back story) no longer includes anything psychology, let alone a SoCal boutique outfit that was easy to engage regarding the problem. And right away here … do you think anyone who actually DOES design would make such a hash of their header?
No more psych …
Encore:
So I decided I would engage it again.
I am going to let the LinkedIn presence just be for the moment, but it’ll get hit by New Years. We’ll see what the Signal account does after that.
Conclusion:
If this were about me, you would not be reading this, because the account operator would certainly be reading it, too. There’d be no value in tipping my hand that way. Being sure that this is a stochastic espionage operation, the most that could happen from this article is some ankle biter deciding to contact that account and let them know I’m on the hunt. **shrug**
Here in the U.S. it’s the Friday after a Thursday Christmas, the deadest of dead time. There are Ukrainians active in my LinkedIn, because orthodox Christmas is the week after New Years, not the week prior. This persona claims Poland and appears to be a younger Millennial, a change which seems to be driven by the near zero value posing as an Asian Zoomer girl. There used to be a bunch of them, but that trailed off, at least for me, a year or more in the past.
I really should go through my history here and tag every pretext approach article I’ve ever done. In fact, that’s a darned good activity for a super slow Friday afternoon, so by the time you read this, there should be a clutch of similar work behind that link.