Sapper Labs Cloak Evolves
A daily driver for me, maturing nicely.
Exploring Hunchly Cloak ten weeks ago seems like a lifetime, but the arrow of time only goes one direction. This would normally be a Tool Time thing, but we’ve arrived at a place where secure operation is not optional. Today I popped in to look at a bullshit “resistance” recruiting effort.
And I saw some exciting new stuff …
Attention Conservation Notice:
This is another review of a prerelease Sapper Labs system, no word on when it might be generally available. So if you’re in need of a solution, this is information in principle, not something specific you can implement immediately.
Features:
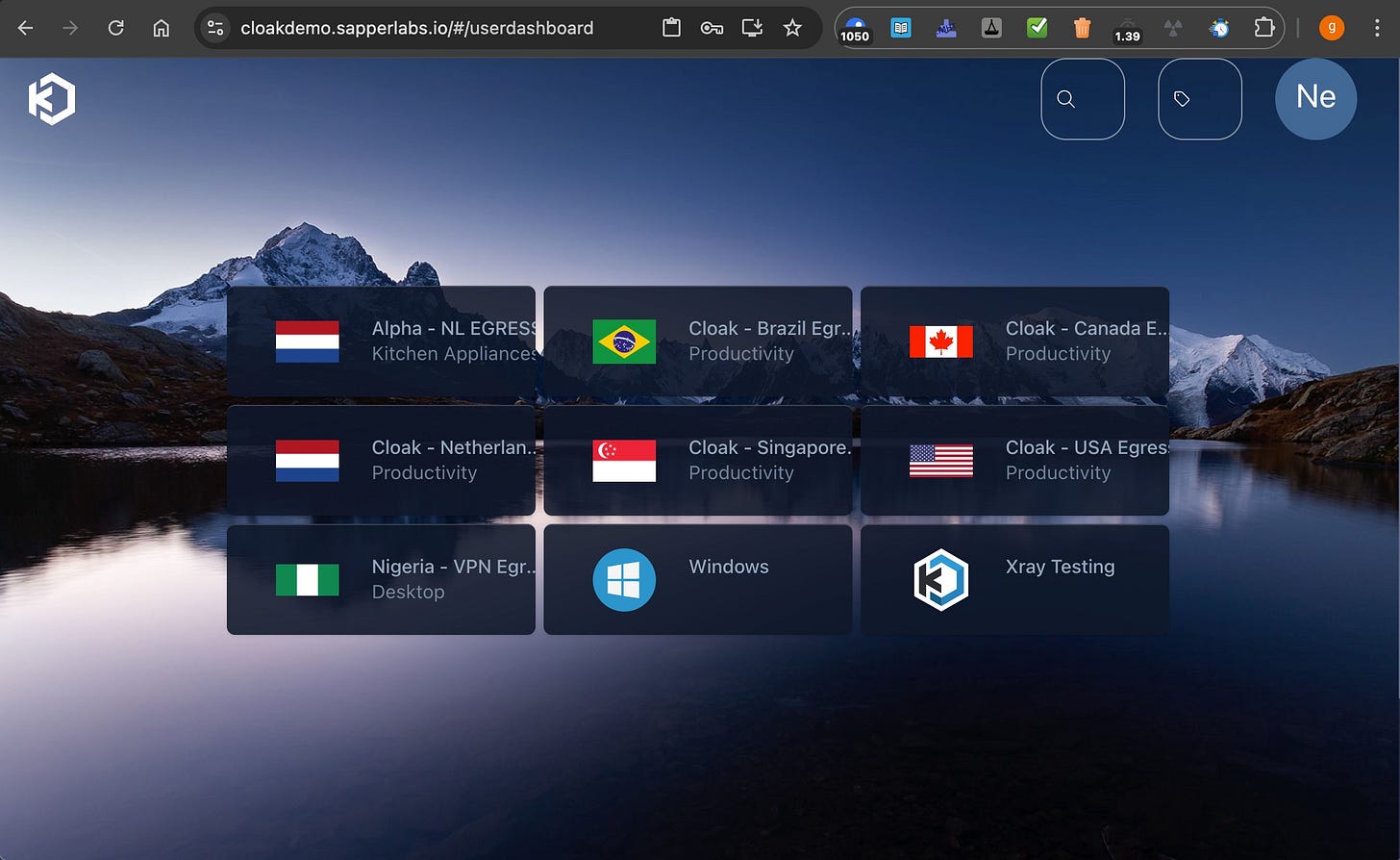
The various Cloak exits have been there, and I can’t stand Windows, even when it’s captive like this. The Nigerians VPN Egress and Xray Testing are new.
And here we see one thing I asked for - TailScale in addition to the other VPN protocols. The objective here is simple - if you can create a TailScale setup, maybe you can use HeadScale … and then arrange your exit to be a burner phone? I can replicate this now with a Linux VM on a Linux host, but that requires 1) Linux, 2) skills most people don’t have, and 3) it won’t work on a Mac. This looks like a thing that I could guide groups into using without constantly worrying that they’ll slip.
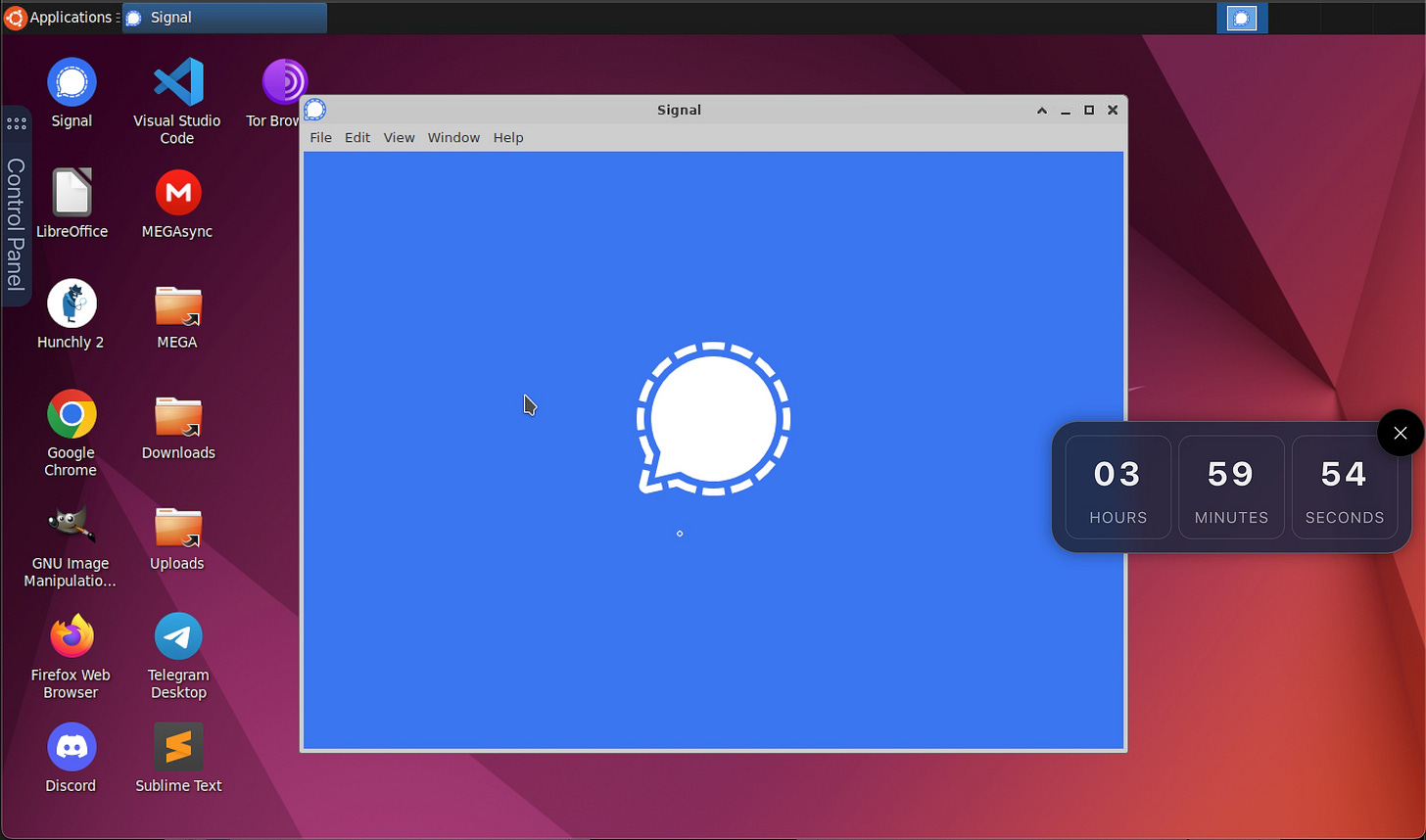
The other big ask was getting Discord, Signal, and Telegram available as part of the default install. Xray is NOT NOT NOT ready for prime time at this point, but I see the three things I really need in here in addition to Hunchly, so it’s headed the right direction.
Cloaking Considered:
When I first started using this I assumed Cloak meant the overall Kasm platform, but after I posted Exploring Hunchly Cloak I got corrected - the Cloak in this case is the network function that enables multiple exits. They don’t say precisely what they’re doing and after the first day of using it and paying attention to network behavior/performance, I still don’t know what it is either.
Cloak exits are something they provide. There is a large customer setup that uses this same setup, but it’s got … stuff … to which I am not privy. I presume there’s bespoke “looks like it originates HERE” as part of that.
One of the concerns when using an IP concealment service is that the exit will get noticed, then correlated, then monitored or blocked. A system like this that’s not full of people trying to circumvent streaming restrictions is more stealthy, but if you’re putting a lot of attention on a wary target, you’ll get made. My request for TailScale support was specifically so we could use the hardened remote desktop while doing our own thing for exits.
I do not know if that’s possible yet, but shifting from Linux to Mac puts a lot of constraints on my networking, so I’m going to explore this in detail.
Conclusion:
The bullshit “resistance” organizing thing taking a week to show up on my desk was pleasing to me. That’s a whole week since the election where no one in my circles saw something like that, and when they did it was promptly reported.
The summer of 2020 was the beginning of the end of my having anything to do with walk on talent. There are just way too many dipshits with time to play infiltration games, and I am fairly distinct, so easily spotted. The relatively few things I’ve done since then have been advisory in nature, and I know I’ve been made here and there, because I was intentionally running a little bit loose. Those bits of bait either didn’t make it very far, or were seen as toxic in nature, and not pursued.
This is a strange new world we’re in, one where I’m glad stomping IRCG has been the notable thing I’ve done in the last twelve months. Every time I think the second installment of MIOS: Iran’s PressTV is going to break there is another YUGE revelation and it gets pushed back again.
But whatever comes next, it’ll be nice being able to dispatch people and not constantly worrying that they’ll make a misstep and lose control of their systems.