Prepared Prowler
Hunting sunrise to sunset.
Some of these articles are written well in advance of posting. I closed the editor on Regarding Your Ass this morning, opened my email, and I was immediately confronted with three different situations that required me to go prowl around the internet. Without disclosing clients:
A person mistakenly “invested” low thousands via wire transfer.
A professional found incorrect news of a license suspension.
We’ve entered silly season, so I have a political front group to sniff.
What I suggested to you in RYA was to get a separate phone, cell service, and a laptop. I do have that but it’s not the right tool for these problems. So without further introduction, let’s dig into the setup I spent twelve hours strapped into today.
Attention Conservation Notice: If you can run your own DNS server, fire up a virtual machine, build a fail closed OpenVPN connection, harden a browser, and you already have a favorite toolkit for attributing muddled online situations, you’re free to go about your business. If you only recognized half of the words, this post is for you.
DNS and Network:
I hate internet advertising in general and I double hate trackers and such when I’m poking around online. I have a couple systems that run 24x7 with more than enough power to keep a small virtual machine going, so I have a Pi-hole DNS server. There are two wifi networks here, one is the whole ass internet no matter how badly it behaves experience and the other offers the Pi-hole ad/tracker filtering DNS server. Hands down the best thing I’ve done around here in a long, long time.
The DNS server is a trifle tricky, because it boots with a static network configuration that’s bridged to both the house network and the special AP, and it doesn’t have a default route. Here’s an example netplan config from another machine. The route you see there is for the entrance to the free ProtonVPN that comes with every free ProtonMail account.
So this VM wakes up disoriented. I have to log in and manually fire up OpenVPN so that it gets a default route through the VPN provider. OK, I guess you need to know this – I trust Proton and Mullvad. Any VPN provider that requires you to load their binary client is probably screwing you in some fashion, any VPN provider that is free is even more not to be trusted.
System:
Assuming the DNS server is running, I can fire up a Linux VM and get ready to investigate. The drill here is similar – the machine wakes up confused and I have to fire up OpenVPN before it can do anything. This is that “fail closed” thing I’ve mentioned. If the VPN is having a bad day, everything just STOPS. There’s no chance it’ll leak my public IP.
I used to have a VM that combined DNS, OpenVPN, and served as the firewall for the special AP. I’ve seen enough stuff about DNS leaks in criminal cases I read that I thought it was wise to have DNS coming from one uncooperative jurisdiction and actual traffic from another. There are a couple additional levels of touchy possible here. You could pick a VPN provider that will terminate a TCP connection and then launder your first leg through Tor, but that’ll give you an erratic connection. It’s possible to hide a VM behind one providing firewall services so that everything the system does is via a SOCKS5 proxy. If lives were on the line I might do that, but it will generally make all those other things you might want to use, like Matrix or Session or Signal or Telegram or Wire behave very badly, if they run at all.
Browser:
I have a fairly standard set of things I do to any Google Chrome install I might use. My bad, even letting the world know I’m a Chrome user, but you’ll see why a bit further down in this section. Here’s a screen shot of Chrome browser extensions.
The ones in there you’d need if you’re going to go sneaking would include:
Adblock – just in case, even if you get Pi-hole running.
CleanURLs – less information is the best information.
DecentralEyes – nope, don’t want to face ADINT.
PrivacyBadger – yet another way to make trackers feel unwelcome.
ScriptSafe – site by site approval of JavaScript, a pain to train, but worth it.
Software:
There are several things I find absolutely indispensable when I’m poking around.
Hunchly is a Google Chrome web capture tool for online investigations.
Maltego is a link analysis package I use for taking notes.
BuiltWith is a fast, free way to examine domains.
Hunchly is $129 a year and worth every penny. You turn it on, it records everything you do. You have a specific name or phone number or keywords, you put that in Selectors, and it’ll tell you which pages you visited have it. This software preserves pages fully, so if something gets taken down you’ve still got a faithful, admissible copy. There’s a note taking feature so you can mark up things as you go, it supports the notion of multiple named investigations, and if you goof on that it will let you easily move batches of pages to the right investigation.
Maltego offers a dizzying array of “transform” vendors. Those are online service providers that you can query about all sorts of things. If you’re just starting you’ll likely be using the free Community Edition with its super crippled no more than twelve items transforms. That’s actually tolerable for this work, because a large potion of what you would want to do – recording entities and their relationships – is just something you do by hand. And the first commercial version is $1,000/year.
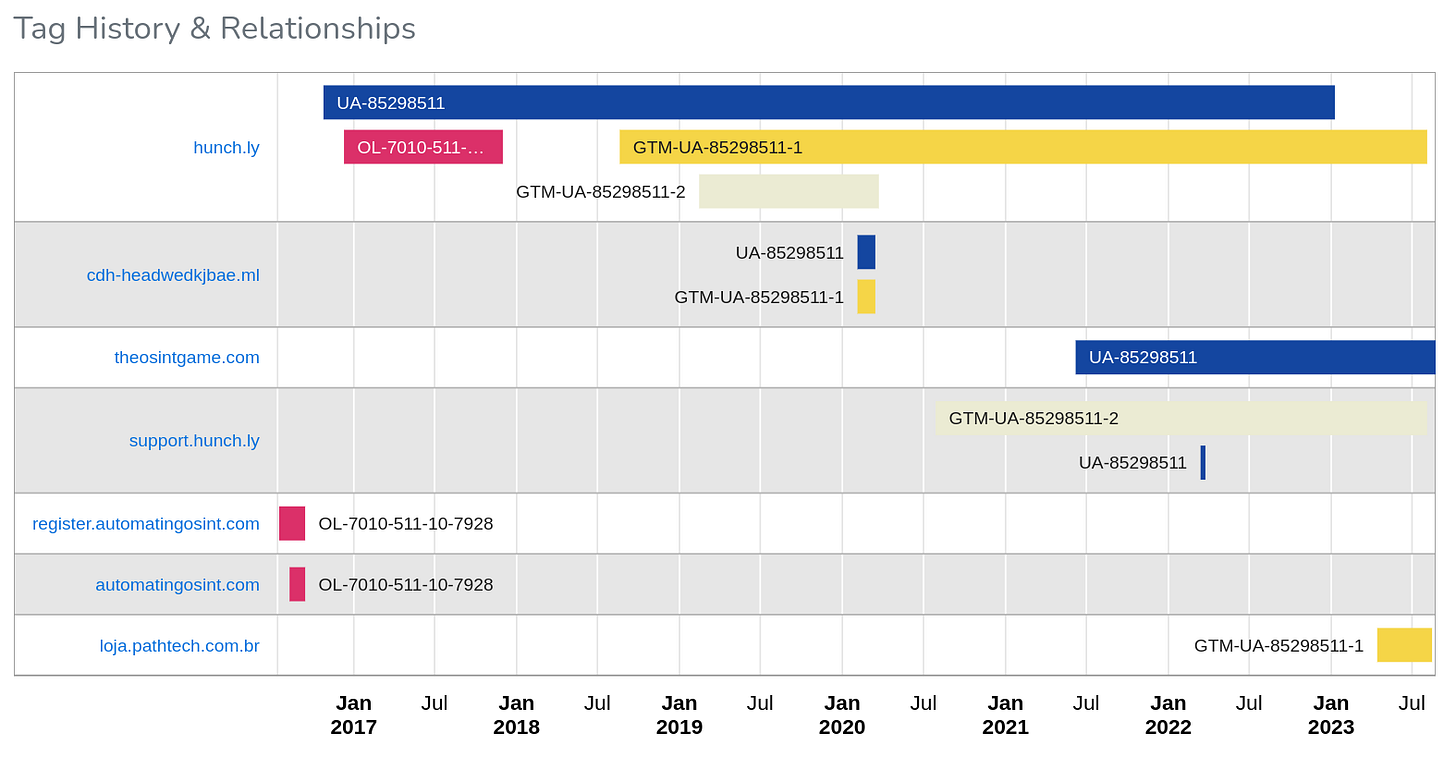
BuiltWith is a marketing tool that’s used by software companies to find leads based on what components are used in a web site. There is a simple relationships tool that does an amazing amount of work for you. As an example let’s check out our friends at Hunchly to see what else they’ve been doing.
What you see there are “tags”. These are unique identifiers for tracking services. They’ve been using Google Analytics UA-85298511 since late 2016, they quickly added Olark OL-7010-511-10-7928 a month later, and the GTM ones are Google Tag Manger at work.
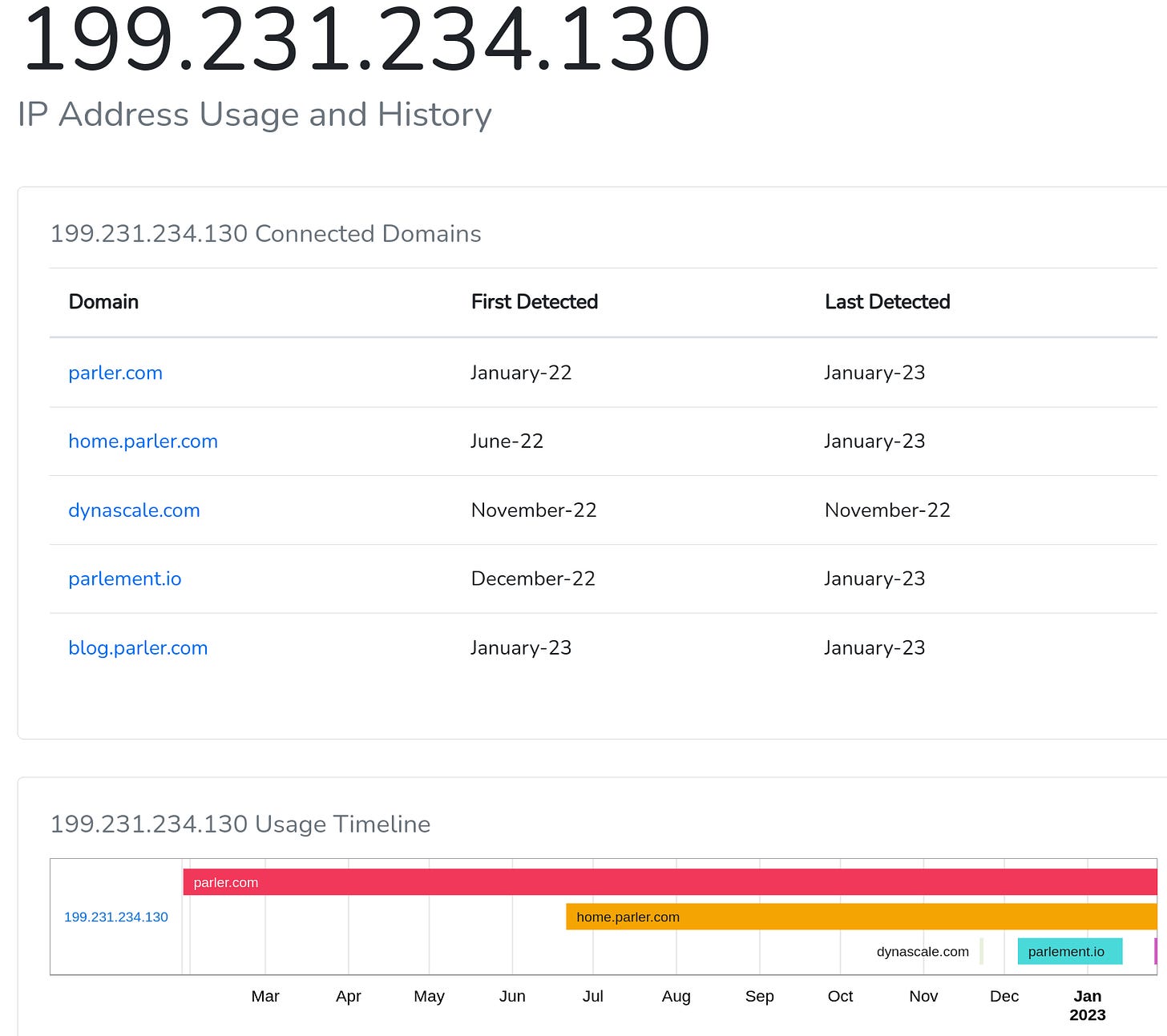
The IP information there isn’t appropriate for a new person to try to get their head around, so I went looking for something a little less esoteric. All of the good stuff I have are things I can’t show, so here’s the first thing I came up with that kinda works as an example – 199.231.234.130 is an IP that Parler used. Here you can see the time frames for the original domain, a new supporting subdomain, and then a whole new domain they purchased.
Leveling Up:
That’s the stuff I do that’s within relatively easy reach for a newcomer. You can get an eval of Hunchly and take that setup for a spin. There are some things I do that require significant financial commitment.
I’ve been a paying Maltego customer since 2012, used to be just $500, a couple years ago the annual fee went to $1,000. There are months where I don’t open it at all, there are months when it’s the right hand half of my main monitor all day every day. I recently had to reinstall and I’m forcing myself to work with free tools for a bit, adding back transform vendors as I need them.
Since I am most often attributing, or doing the recon phase of what a threat would do, most of the transform vendors are just not applicable. The big exception is RiskIQ, which I refuse to call Microsoft Defender Threat Intelligence. Me having this is like a Cessna 172 owner having an RC-135 Rivet Joint they can take out for a spin when they’re feeling curious. This tool is the eye in the sky – it sees most everything you could want to know about any group of web sites or a hosting operation. You can get the free version to see what it does, but I have to issue a WARNING here.
There are a couple of people out there who have the free RiskIQ and they make up amazing fairy tales about the relationships between the fifteen sites they are limited to seeing on a given IP address, say 104.21.44.77, as an example. That’s part of the Cloudflare CDN system and as a commercial user I see 2,076 domains associated with it. The point here is that if use use the transforms from the Community Edition of Maltego, or RiskIQ’s free offering, you will almost certainly make a fool of yourself in the process. Those are for learning, not for heavy duty work.
BuiltWith also has a limit, but at 500 items it’s generous, and if you find one of the “swamp” IP addresses or tags associated with many domains, it will simply give you an error rather than a partial response.
Results:
Recall that I had three things I needed to inspect.
A person mistakenly “invested” low thousands via wire transfer.
A professional found incorrect news of a license suspension.
We’ve entered silly season, so I have a political front group to sniff.
I knew the wire transfer was a lost cause within the first three minutes. I don’t talk a lot about hunting grifters but it’s pretty common tasking. As an Iowa farm boy, if I see a skunk out during the daytime, even if it’s not on my farm, I’ll get the shotgun from behind the seat of the truck and put the poor creature out of its misery. For you city kids, daytime skunks are rabid skunks and they’ll bite your cats, dogs, kids, etc. The victim in this case sometimes solves problems for me, so I spent four hours on it and they’ll get a nice note when I get this guy’s bank privileges revoked.
The license stuff was a real head scratcher. A squeaky clean pro found their name associated with disciplinary action from their profession. This is one of those sites that automatically scrapes public sources and republishes them for the sake of SEO. This was also about four hours and at the end I had identified the web site developer, all of his other customers despite a proxy registration of the domain, thanks mostly to BuiltWith, and I think a quick call next week will resolve it. Based on what I’ve seen he goofed importing public data, there were a number of … curious things … in the records presented.
Every political party in every country has a subset of campaigners who will spoof being their opponent in order to gather information or to sting them. The web site here was “slippery” – not their first rodeo, and even with my fancy tools I couldn’t get at the operator. We’ll talk next week about what next steps might be.
Conclusion:
I am a … journeyman in this area. I’ve operated ISPs, hosting, and I’ve supported commercial SEO and audience tracking, so I know the build side of the business. I have a handful of tools I’ve used between six and twelve years, so I quickly get to the point where I know some things, and have enough experience to be aware of my “known unknowns”.
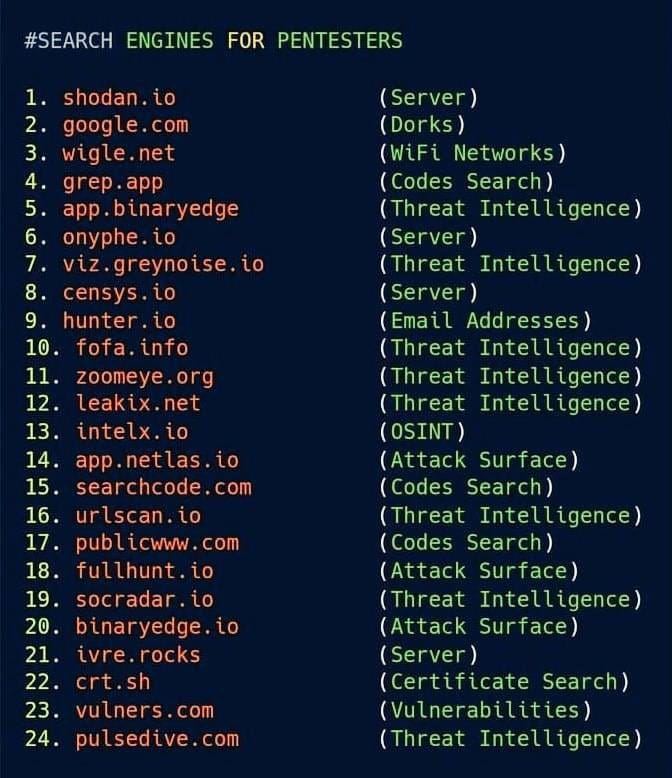
Even so, I want to go faster, further, and harder. I’m doing things with Maltego using unfamiliar transforms and I took this screen shot about six months ago. The work I describe here is the recon portion of a penetration test, so not all of this is applicable, but if I find another tool in that list that serves me as well as BuiltWith, it will be a significant upgrade.






You’re the hunter, who’s the prey?