Phase-based Tactical Analysis of Online Operations
We have a workable doctrine to study.
When a U.S. Army units deploy they are executing a “doctrine”, they’ve got an operational plan based on what they learned from TRADOC. Our responses to what the Russians call “operations technical” and “operations psychological” are, to use another militay acronym, FUBAR.
CYBERCOM collects and squats on vulnerabilities in systems, counting the ability to employ them against opponents as more important than local hardening. They’re counting on law enforcement, our vigorous economy, and geographic isolation to protect us. The results are mixed, at best.
If you examined my recommended links, you can see Paul over at Truth About Threats providing daily reality checking of our utter lack of influence operations capability. Combat ineffective, the rusted, broken hulk of US Influence Operations is lengthy, but if you only have time to read one excellent piece in order to grasp the problem, that’s the one.
During September we covered some basic kit and methods suitable for small groups of irregulars who want to engage in the much needed whole of society response. Technology related stuff is going to turn up in Tool Time whenever I encounter something that’s worthy of sharing.
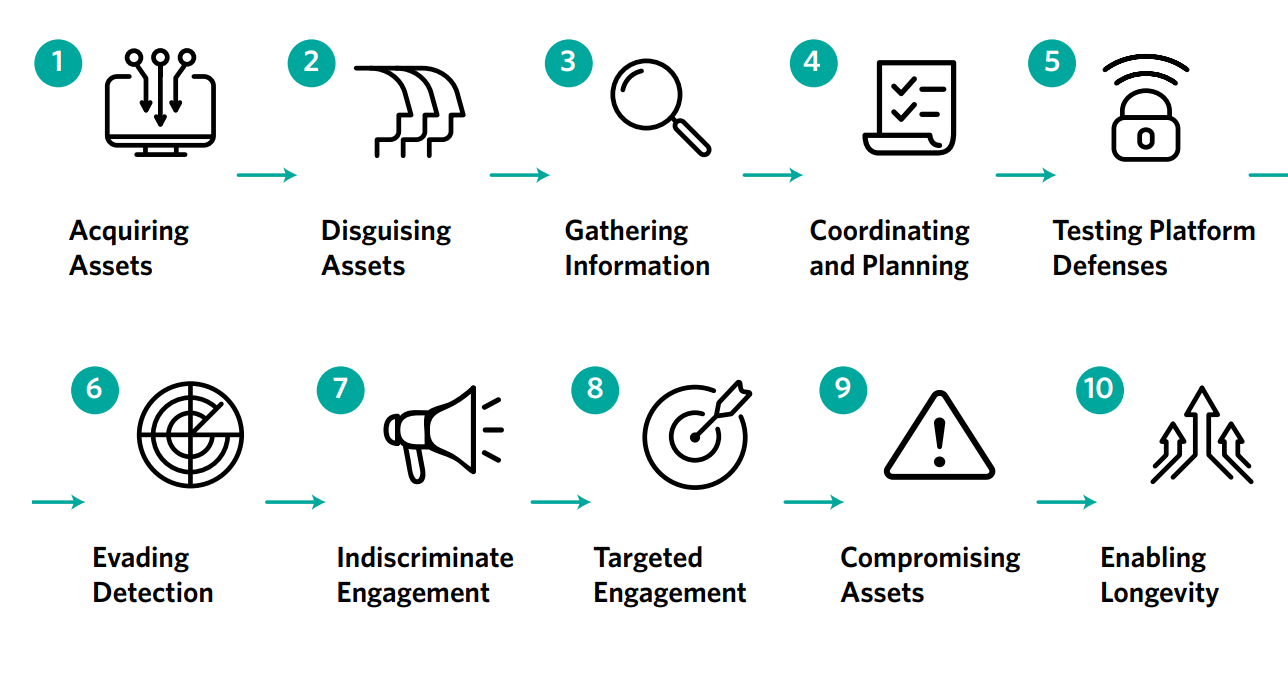
But the main thrust of our activity here is going to be exploring The Online Operations Kill Chain from the Carnegie Endowment for International Peace. They offer a ten phase analytical model, we’ve got twelve weeks in 4th quarter, so this is the focus. I’m going to look around for things that fit the various phases and then write about them. The tempo will slow dramatically – one or two articles a week instead of the daily September boot camp.
Attention Conservation Notice: We have a direction here based on a well researched document from some recognized experts. The next three months of content will focus in this area, so if you’re doing it, keep reading. If you’re commissioning work like this, maybe just read the intro so you’re aware of what’s here and can come back for more when you find the need.
The Ten Phases:
Those Ten Phases are:
Acquiring Assets
Disguising Assets
Gathering Information
Coordinating and Planning
Testing Platform Defenses
Evading Detection
Indisctriminate Engagement
Targeted Engagement
Compromising Assets
Enabling Longevity
The paper is written from a theater level view, so not all of it will be applicable to half a dozen friends in a chat room, but there are good lessons in all of it. If you’re doing serious work you’ll either be early to spot a large effort, or part of a broad response against one.
Conclusion:
This post is both short and late because I’ve been busy with the ONPASSIVE scam, I recently acquired a new phone, and I’ve learned some things about cell phone networking. I’ll be back later this week with a post covering how this works in terms of the first two phases and there will be a Tool Time about the trends in improving cell phone usability.



https://www.lawfaremedia.org/article/everything-you-know-about-vulnerability-equities-process-wrong