NAFO's D.I.L.D.O. Of Consequences
The Directorate of Intelligence Logistics & Disinformation Operations
I first mentioned NAFO precisely one year before our upcoming election, and I credited MIOS: Iran’sPressTV to the Canine Intelligence Agency. This name a jab at the various extremely online loons who attribute any competent amateur activity to America’s internationally focused intel agency.
The CIA acronym is overloaded in so many ways, so today, in honor of ANOTHER high value target getting bit sans any warning bark, we’re gonna talk in a general way about the shadowy group that actually does this work.
Ladies and gentlemen, the Directorate of Intelligence Logistics & Disinformation Operations would like a word …
Attention Conservation Notice:
Silly title, silly topic, but those nosy mutts DID just latch on to another major hostile foreign power activity. You’ll just have to put up with the in-jokes if you want a hint as to what’s coming, and how it got done.
Keeping Context:
The PressTV data is proving to be a bottomless treasure chest. There was already another major Iran focused news story that went to the editors and legal well over a week ago, and yesterday morning, as I was sitting around feeling a bit sorry for myself after publishing Michigan Senate: Closing My Oldest File, those playful pups dragged in what looks to be ANOTHER major surprise.
But first, some background …
A significant portion of the work I do is focused on the MAGA Meltdown graph, which just had its fourth birthday. This monstrosity is almost 8,500 entities with 19,500 links. Among those entities there are 1,563 URLs - citations - web links to quality news, court documents, transcripts I’ve made of TV appearances on YouTube. It’s very unusual for me to read something in late 2024 and find the name of a Trump world person who isn’t already in here.
Procedurally, I don’t just update the main graph. When I find something interesting, like the 23rd’s Washington Post piece that shows John Mark Dougan works for Russia’s GRU, I’ll take the time to pull out what I already had on him from and add the new entities and links. Once I’m happy with it, it gets pasted back into the big one.
So 99% of that graph is other people’s work, but there are things in there that made the news because we took the time to make that happen. That’s a royal “we” - I’m in an editorial role, I check what shows up, decide if it’s worth pursuing, then try to get it placed.
If you want to see some of the gritty detail on how graph updates gets done, GraphCraft: Jack Smith’s October Surprise is specifically for Maltego wranglers.
Find Du Jour:
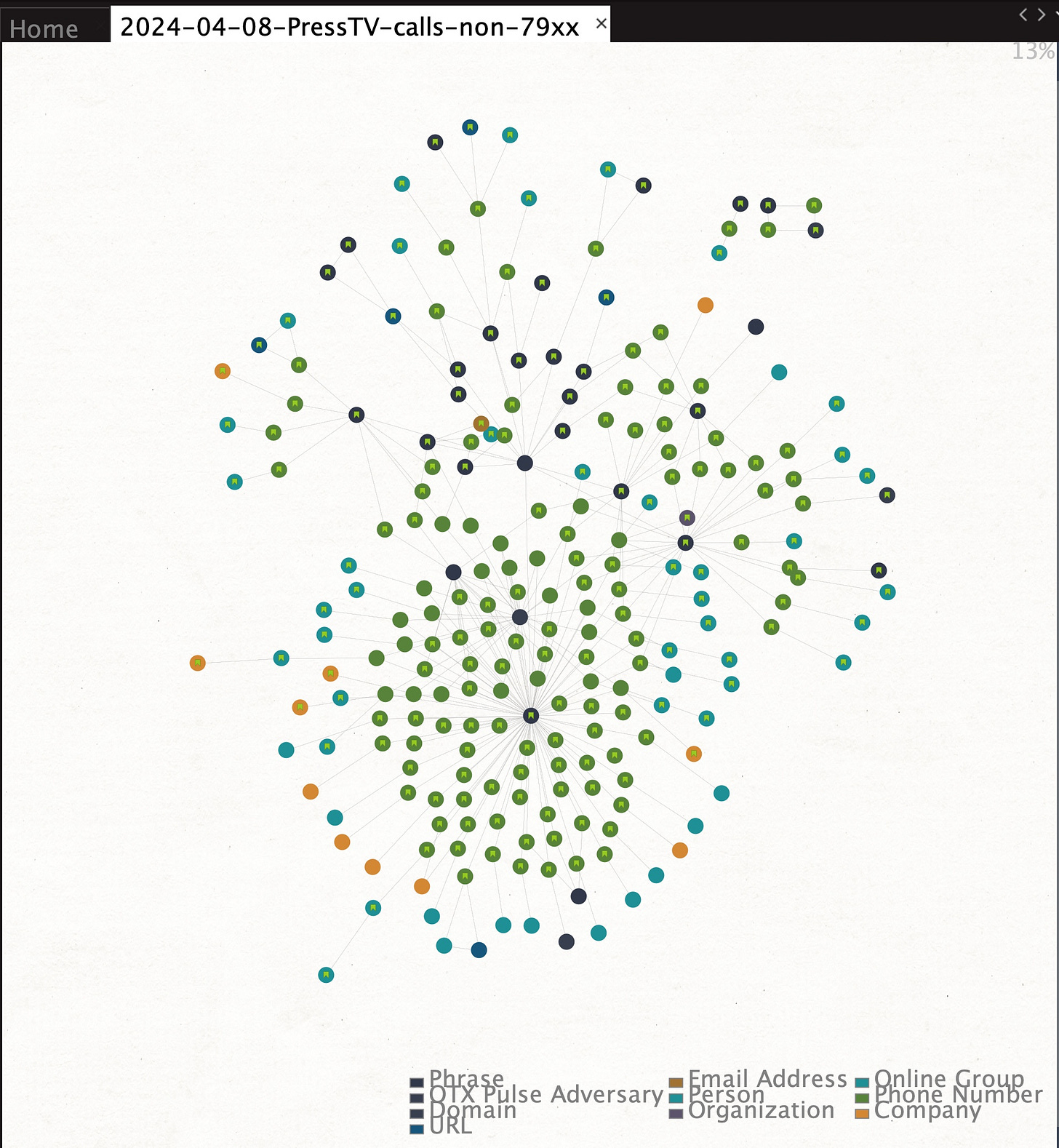
Once I hit publish on Michigan Senate: Closing My Oldest File, I glanced at Signal, and a room that hasn’t moved in two months was at the top of the list. They were talking about a specific issue related to the PressTV data, and were wondering about one specific thing. To which I got to say “Oh, I’ve had that forever, let me find the graph …”
And since I’m a stickler for YYYY-MM-DD-<topic>, it took all of two minutes to find this and get it on screen. Everybody else started on the high volume numbers and known names. Being the old dog leak evaluator that I am, I went right to the bottom of the stack - who got called just once from the administrative extensions?
And when it was done, I sat back and marveled that of the forty four individuals in the graph, two are people I’ve spoken with on the phone, and two I’ve met in real life. All I have to say in my defense is that tRoUbLe mAgNeT is a superpower that does not have an off switch …
There’s a second part to this that involves infrastructure. When there are online influence operations, there are domains registered, web servers provisioned, and unless one is ultra paranoid, there will be configuration errors that will show up in RiskIQ. The average person looking with a Whois related tool wouldn’t notice it, but if you have the ability to see the flow of changes across time, which RiskIQ provides, then sorting out who works with whom is a puzzle, but one that can be solved.
This graph is not part of the recent find, it’s a little snippet of the recent Russian Doppleganger network that I profiled at the start of September. What you’re seeing here are three domains, a number of hosts, the IPv4 and IPv6 addresses they use, and the green square things are IP prefixes. I’m sure it’s a horrible muddle for anyone who doesn’t work in the field, but I don’t have any trouble reading that, or following the little trails of mistakes that leave tracks.
This section is just a starting point and I don’t mind showing it, since there are not a lot of people in the journalism world who do what I do, and when it comes to being party to weird events, I have few peers. This find is D.I.L.D.O.’s and it’ll take a bit to slog through it, but since it’s Iran AND Russia, I suspect editors will move quickly once we have a coherent story to tell.
Conclusion:
All in all, this is a very pleasant surprise - a scoop that nobody else would have spotted, that only we can handle, in a white hot area where we’ve already had success.
I’ve rewritten this section half a dozen times, and that’s a sure sign that I should keep it brief. What began six weeks ago with Grifter: Richard Anderson Sharp III … continues. Your vocabulary word for the day is a chess term - en passant.