DeskNet
A picture is worth a thousand words.
I periodically inform you guys about something I’m building for myself, and those posts usually contain strong prescriptions for you to do something similar. Things on my desk have changed A LOT since I parked my 128GB HP workstation and started using a 16GB MacBook Pro as my daily driver. I am NOT disavowing all the things I’ve said in the past about the value of virtual machine environments as compartments, but impending hardware failure pushed me this direction, and I am learning some things that might be helpful to many of you.
Attention Conservation Notice:
If you’re building out system(s) for yourself, this contains a different path than virtualization. If you’re not, begone wit ye.
DeskNet:
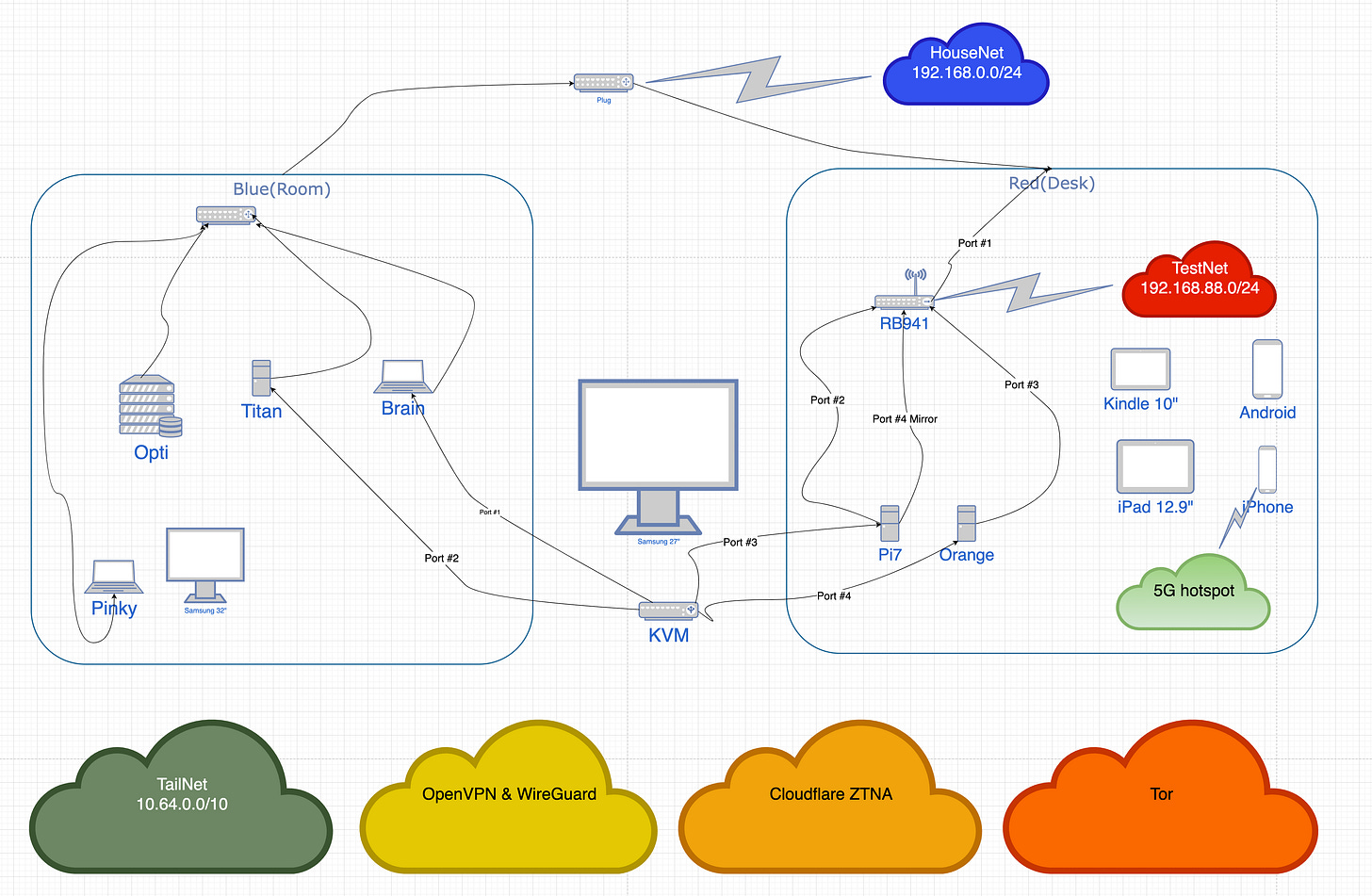
I am working with significant space constraints. My desk is just 48” wide, and I have a 12” wide 6’ long space on the headboard of my bed. Starting from the left, there’s a cable to my dresser on the other side of the room, which has a 32” monitor on it. Sometimes this is work, mostly it’s for movies.
Under the headboard on the floor in the corner sits Opti, a quad core 32GB desktop running Proxmox(naturally headless). Titan is a one liter 32GB machine running Windows 11, Brain is a MacBook Pro that is elevated and out of the way, both are cabled into the KVM. Pi7 is a Raspberry Pi 5, and Orange is an Orange PI Zero 3. There are several mobile devices, I try to keep one of everything, so I can see what someone else is seeing as I’m talking them through things.
The KVM was a $75 impulse purchase in early January, when I thought I was doing really good, and having it is a life changing experience. I’ve had setups like this in data centers in the past, but never a “just flip the switch” on my desktop. Prior to having it I’d be crawling around under my desk, or maybe manhandling it back 18” so I can get to power and ethernet jacks, then once my experiment of the moment was done, I’d reverse that procedure. Thusly a lot of things never got started.
Now I can simply press a button and move from MacOS to Windows to an ARM machine running Ubuntu, and then finally there’s this weird Orange gadget. If I have a sudden impulse to check something, just *click* and I’m doing it. This is enormously freeing.
The other thing to notice in that diagram is the machine named RB941 - that’s a four port MikroTik RB941 that also provides WiFi. It’s cabled directly to the house network, Pi7 gets one line for internet, the other for its sniffer, Orange gets the 4th line, and the mobiles can be shifted to TestNet if I want to observe their internet usage.
I can immediately observe WiFi device network traffic and if I found need to do the same with MacOS or Windows all I need to do is stand up to move one patch cable.
All in all it’s a pretty nice lab setup for me.
Networks:
There are two methods of internet access, the cable modem that’s not pictured and the 5G hotspot provided by an iPhone 12. Both ethernet and WiFi access are readily available. HouseNet is purely for access, while TestNet provides a controlled, observable environment.
Above those foundation layer networks there are four types of virtual network in use. I’ve long suggested either the free service that comes with ProtonMail or the paid Mullvad VPN. That had been OpenVPN, but now WireGuard VPNs have matured to the point where that is what I am using, unless there is a very specific reason to not do that.
TailNet there shows the entire 10.64.0.0/10 Carrier Grade NAT address space, which is what TailScale uses to create it’s mesh overlay VPN networks. If you are simply getting on the internet, OpenVPN/WireGuard is fine. If you are building things at multiple locations and want them to talk among themselves, that’s when you need TailScale.
Cloudflare ZTNA is … less a network and more an admin tool, but it bears mentioning. This is the system I used to create a username/password system for people to access Disinfodrome. If you’re putting up a service on a VPS but you only want a limited number of people to use it, this is one way to accomplish that.
Tor is the very last on the list. People use Tor to creep around unnoticed, or to put up a site that is at risk in some fashion, and must conceal its origin. I sometimes use it in this fashion, but for me it’s been a predecessor to TailScale. You can make ssh accessible via a Tor hidden service, then using the ssh port forwarding feature you have an encrypted, obfuscated path between machines.
Having trouble seeing how to use Tor in this way? Any VPS I manage has a really tight /etc/hosts.allow, which keeps fools at bay, but this is also an admission of who may be using it. If ssh runs as a hidden service, that eliminates that threat. There have been times I’ve rented a tiny VPS and used it to present a service running elsewhere to the internet at large. Think “Open Semantic Search” for people who are really not into sharing their IP address or email … and they’re the sort of folks I don’t want to have pawing at my systems.
A Fifth Wheel:
If you read Wheels Within Wheels you know I’ve been tinkering with two other networks besides TailScale. The radio stuff doesn’t matter in this context, but IPFS certainly does. Once I get the last kinks out of the MikroTik I am going to be spending time running some IPFS stuff, going deep into what it would take to attribute activity there. I think it’s hard, like “getting at stuff on Tor” hard, but that’s fine.
Once I feel I can move in a safe, sure footed fashion, this will become another capability in my bag of tricks.
Wetware:
I wrote this, went away for a day, came back, and felt I should slot this in right here. There are immediately obvious implications that I see, which I suspect most of you will not.
If you build compartments, either with software virtualization, or hardware separation, they’ll work as you intended, so long as you are just an observer.
Where people always get into trouble, me included, are in the virtual environments, particularly when multitasking. If you can alt+tab and change what you’re doing, and if you’re acting in one or more of the environments, it is only a matter of time before you slop something across the dividing line. This is how people get caught, every month there’s a high profile goof like this in the news.
As a basic principle, do not multitask/second screen, you’ll be flowing along through your day, then *BANG* you’re short a couple of toes. Back when I had a public presence on Xitter, if I had to do something else that involved another account on that site, I would set the virtual machine involved to full screen mode. That’s quite a bit better, but if your VM has a shared clipboard with the host, same as above … just cruising along and then *BANG*.
The hardware KVM is a much better choice. Right now this is just for support and testing, but if I ever did need to go creeping around, it would be great to press button #4, get that little Orange Pi moving, and enjoy that it has zero connection to anything else. If I had the budget to go out and get a maxed out $8,800 Mac Studio … no virtual machines for lurking, I’d get a pack of SD cards and build easily swappable hardware environments using a Raspberry Pi 5.
Conclusion:
A machine that can do a lot of virtualization is either going to be expensive, or older.
But if you already have a desktop and want to add a separate compartment for lurking, there are plenty of two port KVMs that are under $40. You could just use whatever VPN, OR you could level up by employing an RB941 as a fail closed VPN device. You’ll likely end up needing a couple cables, but you can get all of his done for around $100.
That second system could be an older laptop you no longer use, an Ebay find, or a Raspberry Pi 5. If you’ve got a pre-Windows 11 machine, it’ll do just fine with Linux. This is what I added in January - comes with Windows 11, and I was pleased to find that all I need is another NVMe stick and I can get it running Qubes as well.
There are endless reasons to lock your stuff down tight in 2025. This Substack has been steadily addressing both the “I don’t know how” and “I can’t afford that” excuses.
It’s not that hard. It’s not that expensive.
And failing to get it done can be awful in ways most of you have not experienced. Yet.