Alethea: Invisible Ink
A GRU disinformation study.
Later today I think there will be an article about a GRU media asset for which NAFO’s Canine Intelligence Agency helped on the background. I’ve been looking at my queue and there are five other things brewing with a Russian angle to them.
MIOS: Russpublicans still out there, not yet published.
Roger Stone’s Power10 Botnet - even more stalled than Russpublicans.
Ivan Raiklin’s Shortlist - in process and it’s got Russians in it.
A U.S. media operation likely violating sanctions with RT.
A U.S. financial sector firm with curious Russian ties.
While I’m urging these things along, I’m also looking at what others are doing in the area, and I recently discovered Alethea’s report entitled Writing With Invisible Ink. This is a much more polished thing than the output I’ve produced in the past, but it all looks very familiar …
Attention Conservation Notice:
Just reviewing a Russian influence ops paper, this is rightly filed with the Malign Influence Operations Safari work. If you’re developing tradecraft in this area, it’s good, otherwise just skim and move on.
Background:
Alethea is large enough that they apparently still have access to the formerly free Twitter API, so much so that they can profile accounts in the thousands. I really miss having access to this, but I’ve been working at getting my historic data available, as I think there’s some value in having it handy.
I did not write about it at the time, but ten days ago I read the Correctiv piece on Doppelganger and I dug into the infrastructure mentioned. This overlaps with what Alethea are finding, but I could not find a list of the 81 domains they reference in their study. The lone clue is on page 6 of the report.
The sites cloned by the operation show some of the important geographic targets for the Russians, including cloning Fox News, The Guardian, Le Monde, and Spiegel.
There were 34 available in the Correctiv report, seen here, so there’s a degree of matching to be seen.
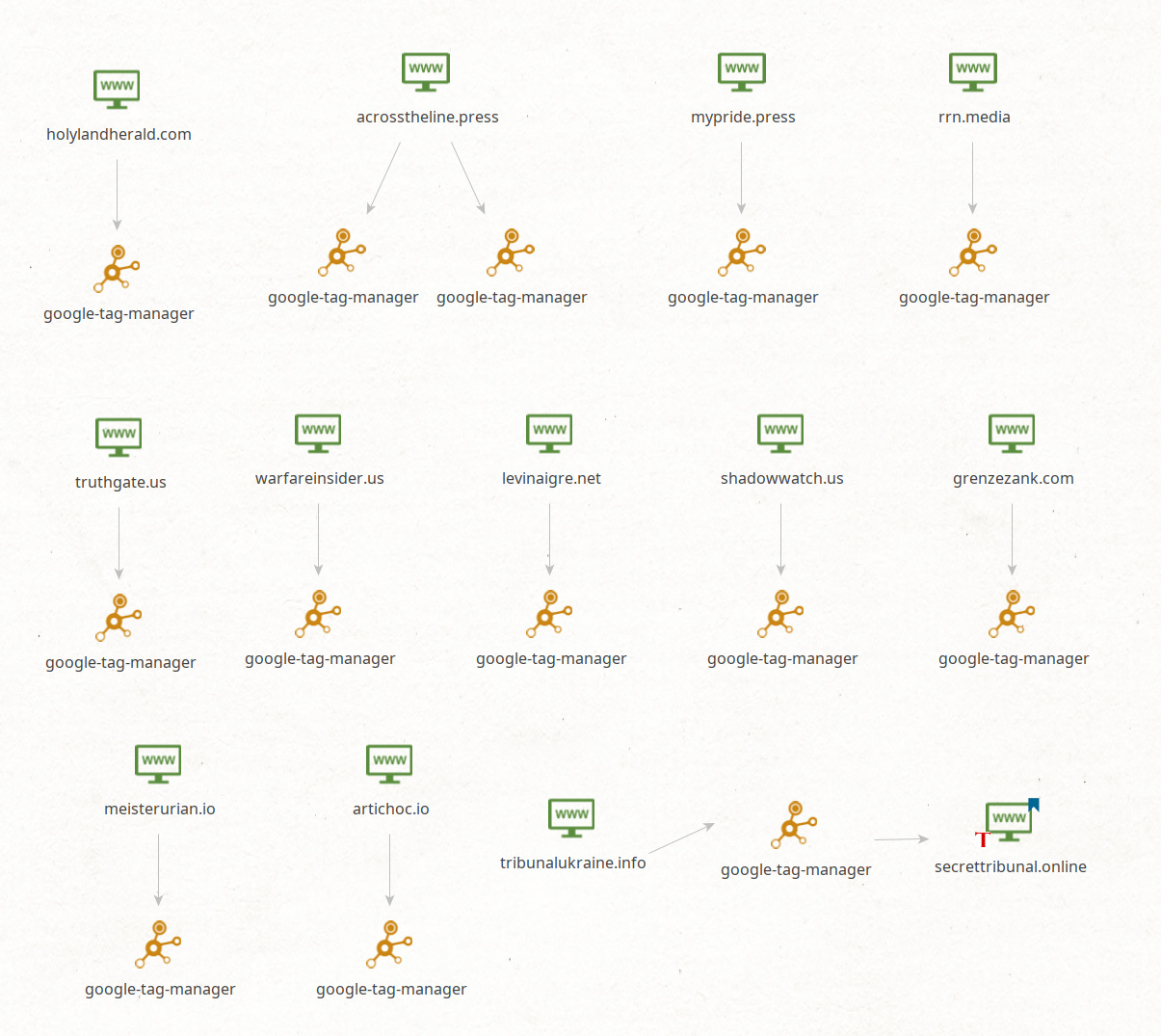
Using Maltego’s L1 footprint machine, I found that what is still visible in this network is entirely behind Cloudflare.
Given what was revealed by examining martech in MIOS: Russpublicans I took a look at the relationships between these domains. There was a notable lack of Google Analytics, and the only thing I uncovered was this secrettribunal[.]online domain.
I really wish the Alethea report contained more info on the domains that were involved. They repeatedly mention Doppelganger, but I’m not seeing anything that looks like a manifest.
Actual Amplification:
The methods being used avoid Twitter’s basic interdiction methods. They avoid API based references to other accounts and post things directly. The domains used redirect to other things that redirect again, avoiding showing Twitter’s system an immediate problem. If I had my old system running and a few seed accounts from this set, it wouldn’t take long to identify the rest of the network, but that’s an “if” with a $5k price tag associated.
The redirection chaining is interesting - knowing this exists, it wouldn’t be too hard to craft a bit of Python to track through it. But overall I am a bit worried about infrastructure attribution - Google Analytics formerly used the main account number with a trailing dash and a digit for each additional property monitored. That’s gone as of July and with it an important form of “entanglement” we used to use for attribution.
This just begs for closer examination of the martech, but since posting Rushing Into Semrush, I haven’t really rushed anywhere. It’s running on a few Substacks, I just recently got access to a paying customer of ours who is using their free service, but trying to get to actually doing an implementation and then running a campaign has been an exercise in frustration. I did recently gain Google Analytics access for a 501c3, but it’s hard to carve out a big block of hours to do something when it’s not clear when, or even if it’s going to produce results.
The other worry I have in infrastructure is the decline of RiskIQ. They’ve retired the API access for Maltego and I wonder how long the web interface system will remain. I’ve looked at Microsoft’s alternative offering and it’s a quintessential Microsoft product - annoying, invasive, not very capable, and immediately grasping for your PII and wallet the minute you look at it. I should probably go around and see what the alternatives are, but I get a bad feeling like anything workable will have a four digit monthly price tag attached.
References:
I pulled the text from the PDF and extracted the domains referenced. There’s a lot of Twitter in this, which frustrates me endlessly, because I don’t have a live account in my daily work environment and I’m trying to keep it that way.
I see a couple Recorded Future URLs, and the best thing is How two information portals hide their ties to the Russian News Agency Inforos, which came from EU’s DisinfoLab. This is very COVID focused, but that’s good - the medical disinformation sector is heavily involved with Russian stuff. And this one has more domains information for me to tug at with Maltego, RiskIQ, and related tools.
It’s interesting to see what gets published directly, what gets mentioned in footnotes, and what’s alluded to but never specified. This is the journalism problem all over again - something important gets found, turned into a report, then the original author squats on the data. I’m going to go looking for a MISP galaxy that covers this area, hopefully there’s something akin to Open Threat Exchange that I’ve just not found yet.
Conclusion:
It’s a good report on a current topic - go read Writing With Invisible Ink. But for me there are a lot of local implications.
Regular readers will recall that I used to operate a Twitter streaming data collection system, and there’s a 220 million tweet/user profile recording on my Figshare of the influence operation that led to the Capitol Siege. That information is described in the Disinfodrome Proffers and I’m working on getting the historic data available again within Disinfodrome. I would really like to wiggle my way back into a place where I have streaming access again, but it’s gotta be a revenue generator, otherwise I spend all of my time digging and not enough time billing.
The change in Google Analytics and the much more worrying happenings with RiskIQ have me slightly on edge. There are other threat hunter systems with historic data, but it would be difficult to reproduce what I have with RiskIQ. I think the commercial rate for what they give researchers is around $90,000 annually. As above, I’d like to wiggle into a place where I get more access, but it’s gotta have a revenue component to it - I have quite enough in the way of esoteric hobbies at this point.
And the thing looming over all this is the GraphRAG upgrade to Disinfodrome. There are things AI could do in this area in a few minutes that would take a human a month of Sundays, but quality control on the inputs is absolutely key. I keep seeing things that I wish I could access with awk/python from the command line, and that is possible, but the learning curve is significant. The only way out here is through, but I have yet to find something local that makes me productive, thus far having ChatGPT as a research assistant is the only thing positive in this area.
It’s 0600 Pacific time as I’m finishing this. Off I go in search of what I’m going to call work for the month of October …